What is Sigstore?
A brief on sigstore - a new approach for signing, verifying and protecting software.
As noted in my post on security scorecards, open source software (OSS) adoption has seen a rise in recent years, but OSS has also been plagued with software vulnerabilities and exploitable weaknesses. Recent vulnerabilities like dependency confusion, as well as software supply chain attacks against SolarWinds and Codecov, have been a wake-up call for the industry. There is growing awareness and need to establish and verify the integrity of OSS packages before integrating them into applications. Security scorecards and the SLSA framework are industry-wide efforts to improve software supply chain security. Today, we'll explore another effort - sigstore.

Sigstore, a project of the Linux Foundation, is a new approach (and hopefully a standard soon) for signing, verifying and protecting software. It offers a set of tools for developers to sign software releases, and for users to verify the signatures. Just like Let's Encrypt issues free certificates for HTTPS, sigstore offers free certificates for source code signing, issued by a dedicated Root CA (Certificate Authority). Sigstore is also backed by transparency logs, making the certificates and attestations globally visible and auditable. Here's a quick look at how sigstore works.
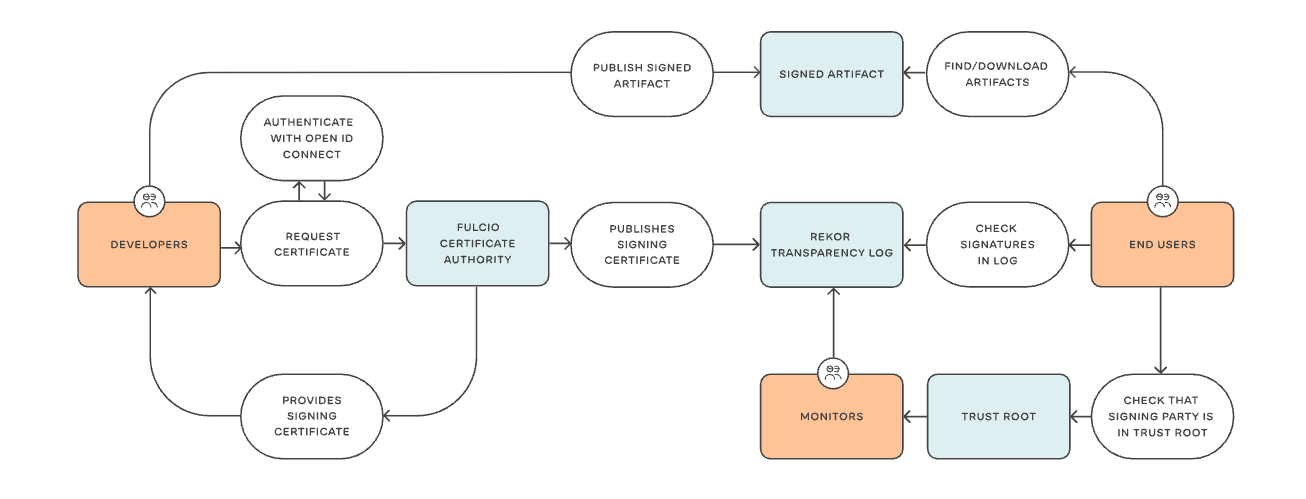
Sigstore relies on the following open-source technologies:
- Fulcio: Root CA for code signing certificates; issues short-lived certificates based on OIDC email address, and publishes them to Rekor
- Cosign: Generate key pair, sign container images and store in the Open Container Initiative (OCI) registry, and verify signatures against public keys. See this post for a deep dive on cosign.
- Rekor: Immutable, tamper-resistant ledger of signed metadata; fulfils the signature transparency role
Obviously, the success of any new project is largely determined by adoption from existing/popular community projects. Kubernetes, a popular open-source project, recently offered a huge vote of confidence, announcing that v1.24 would include signed sigstore certificates for all Kubernetes binaries and images. Another behemoth, GitHub, announced that all npm packages will start using sigstore. In fact, GitHub is also working with sigstore to link npm packages to their source repositories and build instructions, significantly improving the provenance of the supply chain. Suffice to say, sigstore is seeing rapid development and support, with promising signs of playing a critical role in securing the software supply chain.