The Muggles Guide to Zero Trust Access
The muggles guide to zero trust access, a short compendium.

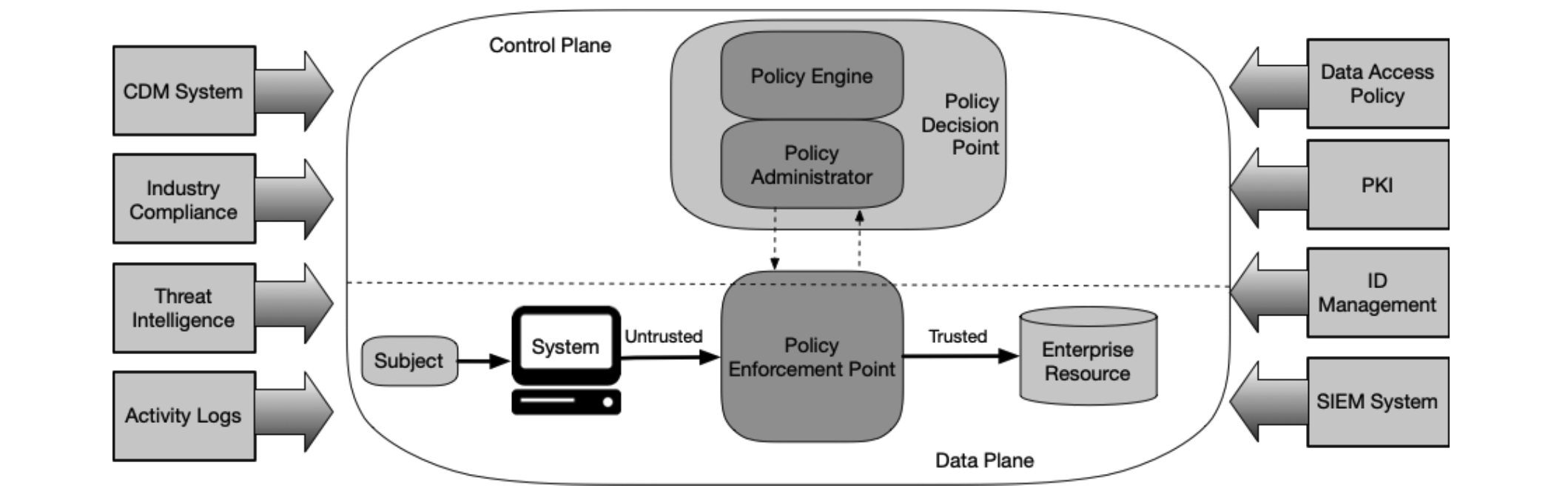
From NIST SP 800-207:
Zero trust is the term for an evolving set of cybersecurity paradigms that move defenses from static, network-based perimeters to focus on users, assets, and resources. Zero trust assumes there is no implicit trust granted to assets or user accounts based solely on their physical or network location or based on asset ownership. Authentication and authorization (both subject and device) are discrete functions performed before a session to an enterprise resource is established.
In this set of blog posts, I cover zero trust basics, including the canonical definition from NIST, along with different ways to set up zero trust architectures and to access corporate resources remotely. Zero trust is an evolving domain of security, and I'll update this post with more examples as I write about them.