Remote Server Access with Teleport
A step-by-step guide on remote server access with Teleport.
Managing infrastructure at scale, across heterogenous environments, while ensuring seamless access for an increasingly distributed and remote workforce is not easy, to say the least. To do so while also ensuring that unauthorised users are kept at bay in the face of increasing cybercrime is even harder. Traditionally, organisations have managed remote access to infrastructure resources like virtual machines using a combination of Virtual Private Networks (VPN) and bastion host software. While it does the job, this approach adds friction to the end user experience, and creates operational overheads for the resource administrators. Let's explore an alternative approach using Teleport today.
What is Teleport?
Teleport is an open source project that consolidates connectivity, authentication, authorisation and audit into a single access plane for your infrastructure. It offers identity-based access for users and service principals, fine-grained access controls, and extensive visibility into your infrastructure access and behaviour.
Teleport Server Access is easy to deploy and use, and relies on open standards like X.509 certificates, SAML, OpenID Connect and more. It offers a way to drop SSH keys in lieu of identity-based access, and can enforce multi-factor authentication (MFA), role-based access controls (RBAC) and single sign-on (SSO).
Deploy Teleport Server on a DigitalOcean Droplet
I'm going to use DigitalOcean for this post - if you don't have an account, sign up here. If you sign up using my link, you’ll receive a $100, 60-day credit as soon as you add a valid payment method to your account.
Assuming you are familiar with droplet creation in DigitalOcean, I won't go into step-by-step detail. Basically, you need to choose a plan (4GB RAM / 2 CPU), an image (Ubuntu 20.04), the data center region, an authentication option (root password for now, but non-root user in a real environment) and the hostname.
Once the droplet is ready, select it and launch the Droplet Console as root from the menu options. Run the following commands to update the Ubuntu instance, and install the Teleport package.
# Download Teleport PGP public key
curl https://deb.releases.teleport.dev/teleport-pubkey.asc \
-o /usr/share/keyrings/teleport-archive-keyring.asc
# Add the Teleport repository
$ cat<<EOF>/etc/apt/sources.list.d/teleport.list
deb [signed-by=/usr/share/keyrings/teleport-archive-keyring.asc] https://deb.releases.teleport.dev/ stable main
EOF
# Update package metadata and install Teleport
apt-get update
apt-get install teleportConfigure DNS for Teleport Proxy Service
I'm assuming that you already own a domain to map the Teleport server against. If you don't, head over to Cloudflare Registrar or Namecheap and register your domain first. Next, add an A record (e.g. teleport.example.com) and map it to the public IP address of the droplet you just created. For example:
A teleport.example.com 167.172.56.128
You can use dig to check whether the DNS records have propagated. You can also use the Google Admin Toolbox.
dig teleport.example.comConfigure Teleport for Remote Admin Access
Next, let's configure the Teleport Proxy Service and set up a TLS certificate for the sub-domain. You need to provide an email address, so either you'll need your MX records configured for the domain, or provide a different email address. Teleport uses Let's Encrypt, a non-profit Certificate Authority, to issue free TLS certificates. Let's Encrypt uses the ACME protocol to verify that you control a given domain name and to automatically issue you a certificate.
# Configure the Teleport Proxy Service to issue Let's Encrypt certificate
teleport configure --acme --acme-email=user@example.com --cluster-name=teleport.example.com > /etc/teleport.yaml
# Start the Teleport service
systemctl start teleportThe following settings should get added to your Teleport configuration file (/etc/teleport.yaml). Ensure that your firewall allows incoming traffic on port 443.
proxy_service:
enabled: "yes"
web_listen_addr: :443
public_addr: teleport.example.com:443
acme:
enabled: "yes"
email: user@example.comYou should now be able to access the Teleport web console using the sub-domain i.e. teleport.example.com. Yup, pretty straightforward.
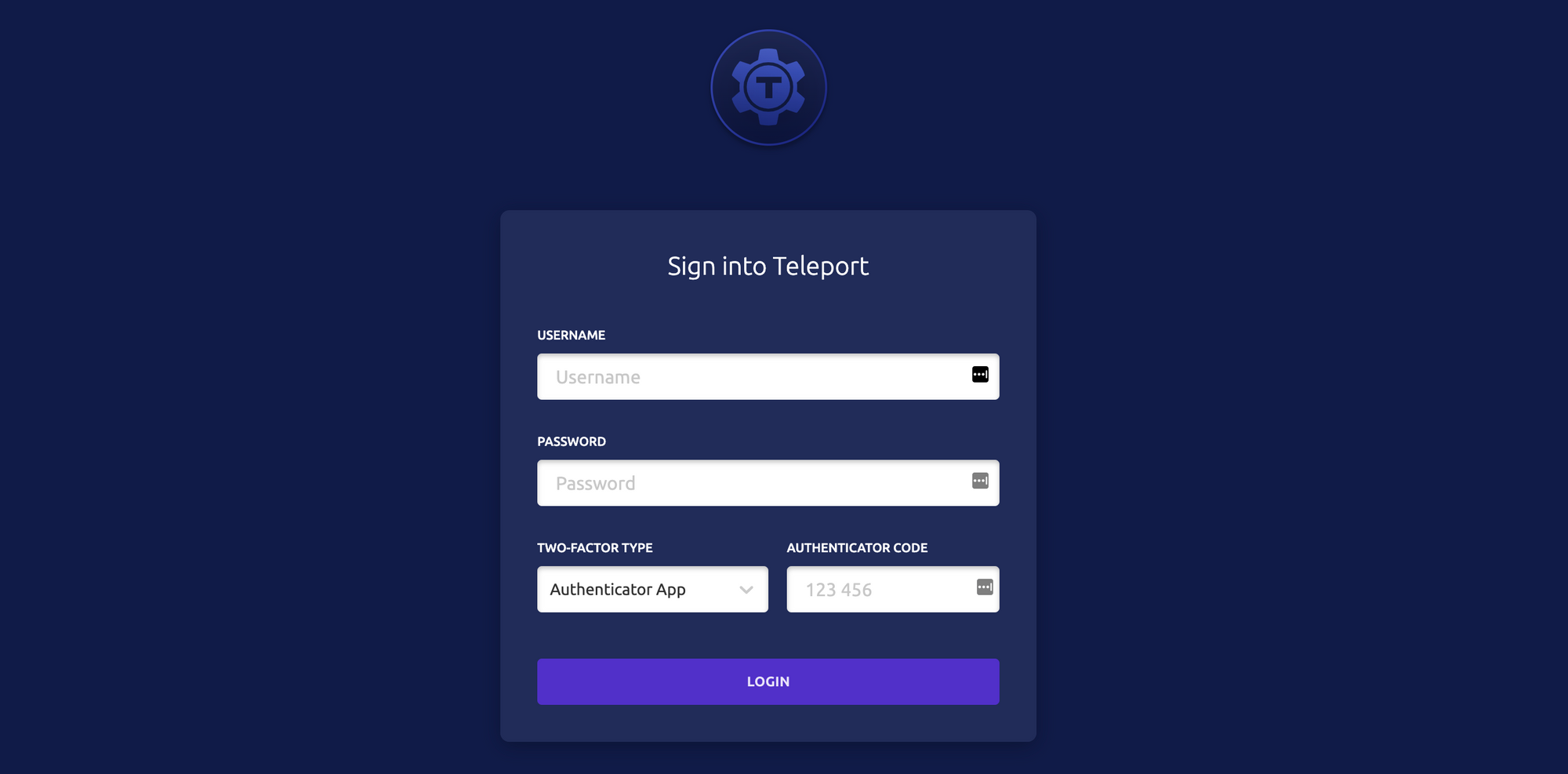
Create Teleport User and Configure 2FA
Create a Teleport user teleport-admin and allow it to log into the Teleport hosts using root and ubuntu user principals. Ideally, you should avoid permissive system accounts like root and create appropriately privileged OS users using adduser <user> first.
tctl users add teleport-admin --roles=editor,access --logins=root,ubuntu
User "teleport-admin" has been created but requires a password. Share this URL with the user to complete user setup, link is valid for 1h:
https://teleport.example.com:443/web/invite/216bb6044876542018834b32kd84b8c99Use the login URL to configure the password and 2FA using Google Authenticator.
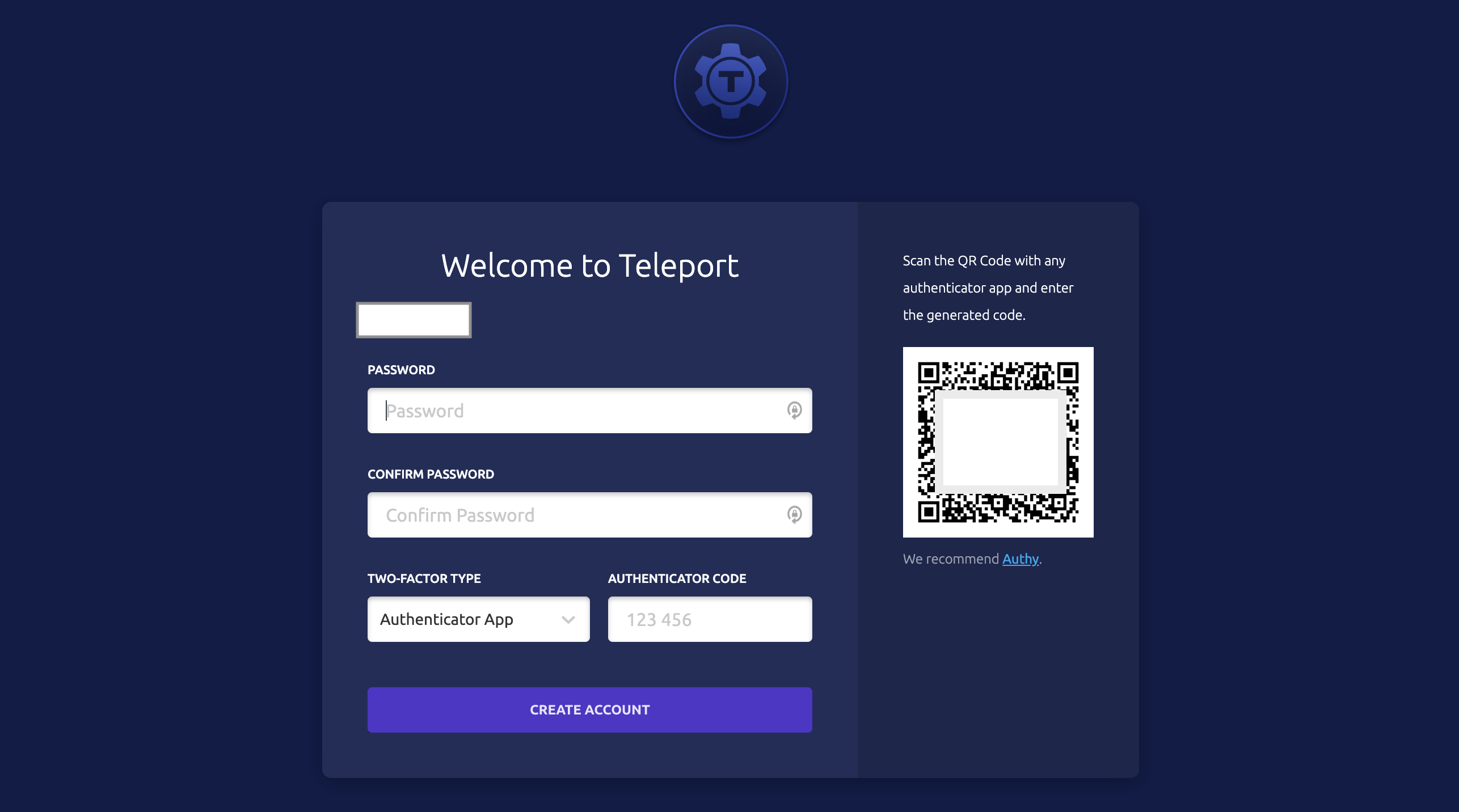
Once you successfully authenticate, you'll see the Teleport servers available for remote access. Click on the Connect button, choose the user you want to authenticate as, and you're in!
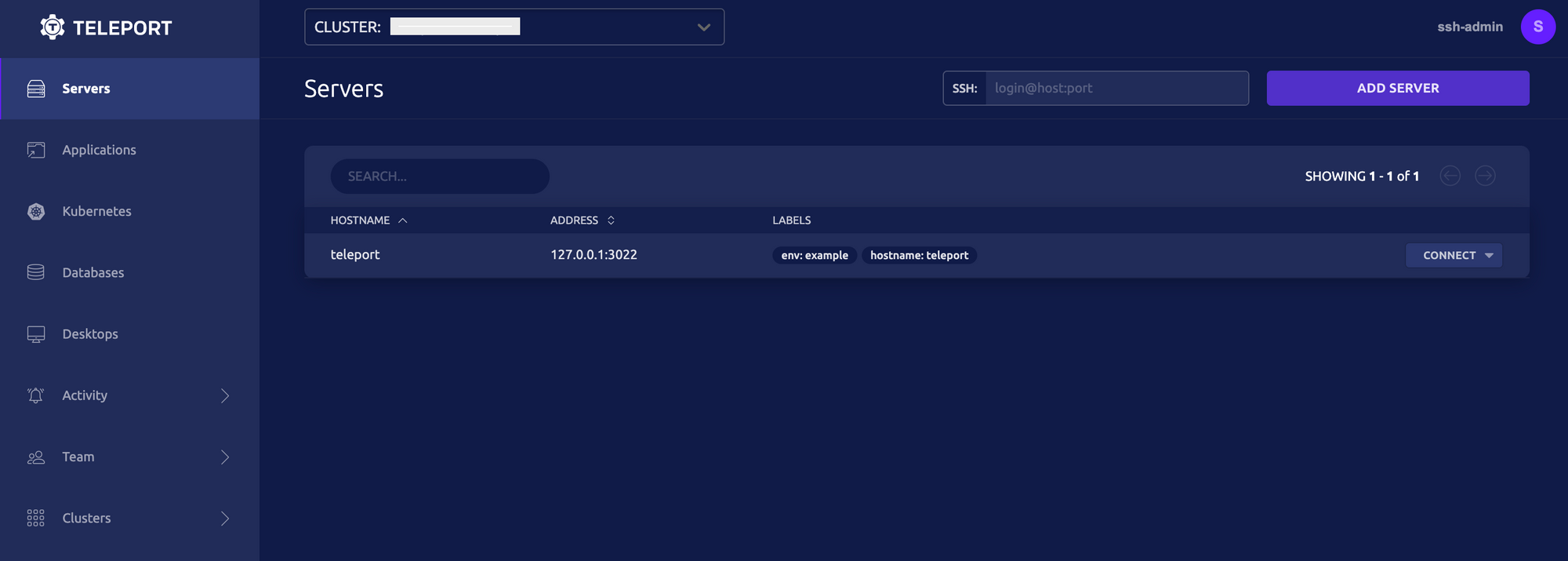
Connect using Teleport Desktop Client
If you prefer not to use the web console, you can also connect to the Teleport server using the desktop client, tsh. On a MacOS device, you can download and run the .pkg installer. On a Windows machine, download the tsh archive, unzip the tsh executable and move it to your %PATH%. Detailed instructions to do this, as well as for running the tsh client on Linux devices, are documented here.
To log in using the tsh client, run the following command. The tsh client will automatically obtain short-lived credentials from the Teleport server and facilitate the login after user authentication.
tsh login --proxy=teleport.example.com --user=ssh-adminIf you found this post useful, you may also like my related post on Identity-based Access to Web Applications with Teleport.