Container Vulnerability Scanning with Trivy
A brief on container vulnerability scanning with open source Trivy.
Automation is a foundational construct of DevSecOps, a concept where DevOps is augmented with security practices early in the life cycle. Scanning the resultant artefacts for vulnerabilities is an essential part of that life cycle, especially if you use cloud-native environments and mechanisms like containers. In this post, I'll describe how such vulnerability scans can be automated using Trivy.
What is Trivy?
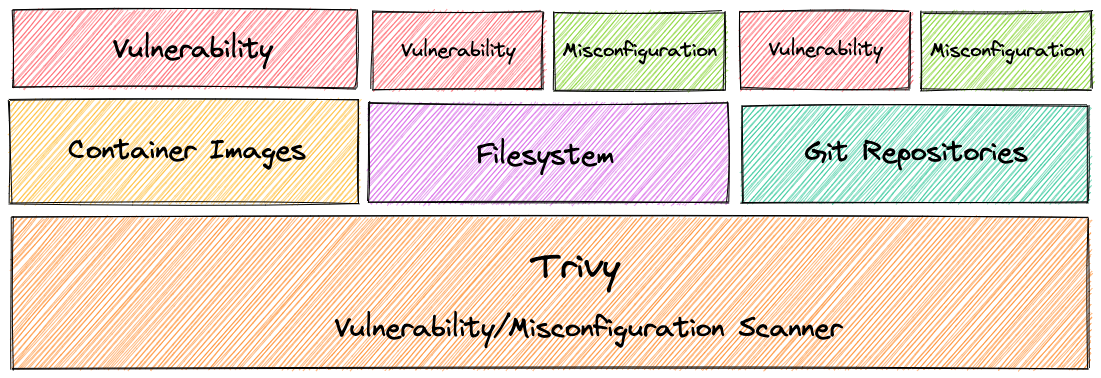
Trivy, an open source project by Aqua Security, is a vulnerability/misconfiguration scanner for artefacts like container images, filesystem/rootfs and git repositories. It has comprehensive detection for OS and language-specific packages, as well as infrastructure-as-code files. Trivy is designed to integrate with your continuous integration (CI) pipeline, before the artefacts are deployed to production.
Deploy Trivy on a DigitalOcean Droplet
I'm going to use DigitalOcean for this post - if you don't have an account, sign up here. If you sign up using my link, you’ll receive a $100, 60-day credit as soon as you add a valid payment method to your account.
Assuming you are familiar with droplet creation in DigitalOcean, I won't go into step-by-step detail. Basically, you need to choose a plan (4GB RAM / 2 CPU), an image (Ubuntu 20.04), the data center region, an authentication option (password for now, but SSH in a real environment) and the hostname.
Once the droplet is ready, select it and launch the Droplet Console as root from the menu options. Run the following commands to update the Ubuntu instance, and install the Trivy package.
# Add repository setting to /etc/apt/sources.list.d
apt-get install wget apt-transport-https gnupg lsb-release
wget -qO - https://aquasecurity.github.io/trivy-repo/deb/public.key | apt-key add -
echo deb https://aquasecurity.github.io/trivy-repo/deb $(lsb_release -sc) main | tee -a /etc/apt/sources.list.d/trivy.list
# Update the package metadata and install Trivy
apt-get update
apt-get install trivyScan Container Image for Vulnerabilities
Scanning container images using Trivy is quite straightforward. And fast!
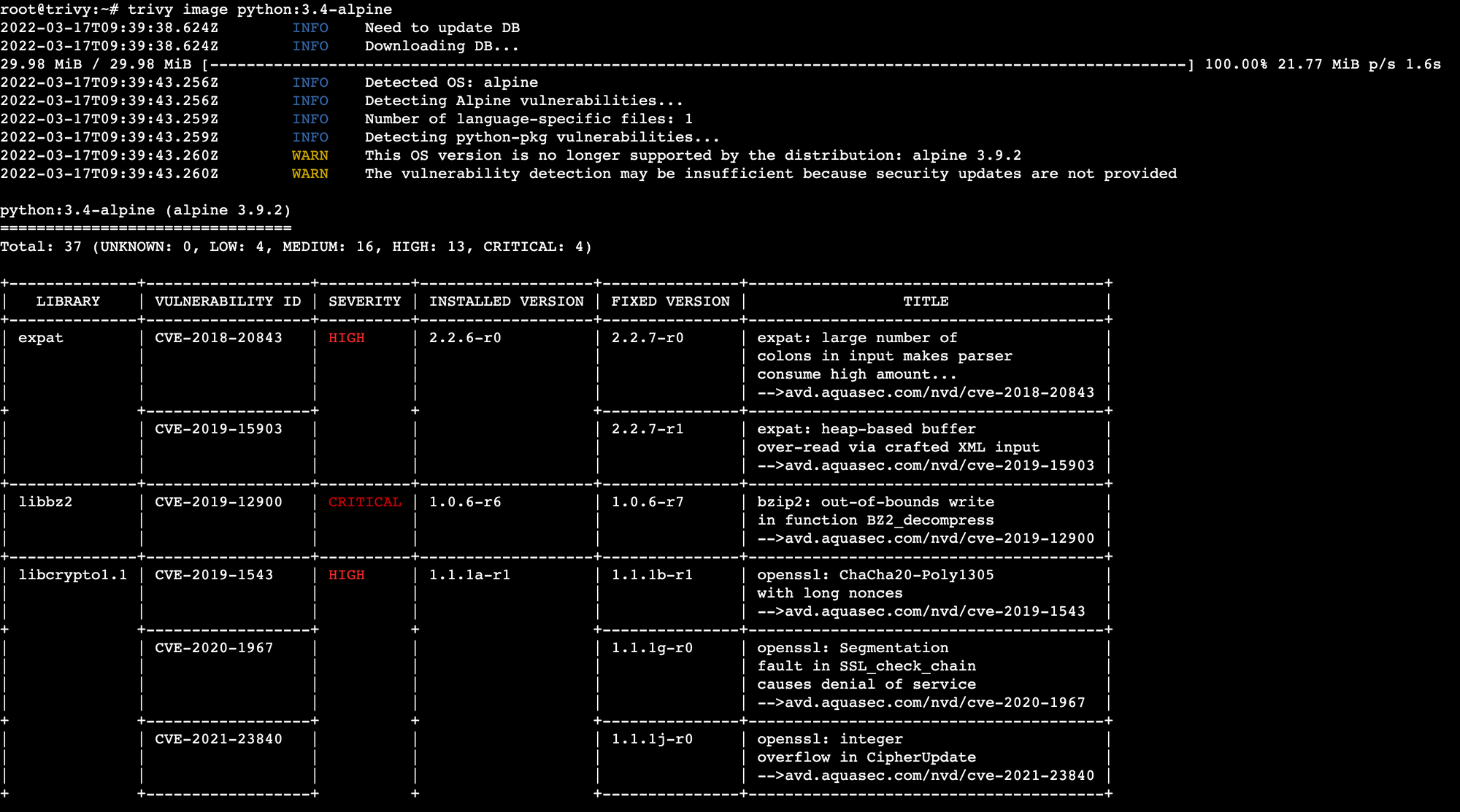
trivy image [IMAGE_NAME]Sample (truncated) results of a vulnerability scan on the python:3.4-alpine image are shown below.
If you prefer the output as a JSON file instead of the default tabular format, run:
trivy image -f json -o results.json [IMAGE_NAME]Scan Git Repository for Vulnerabilities
To scan a remote git repository, run the following command.
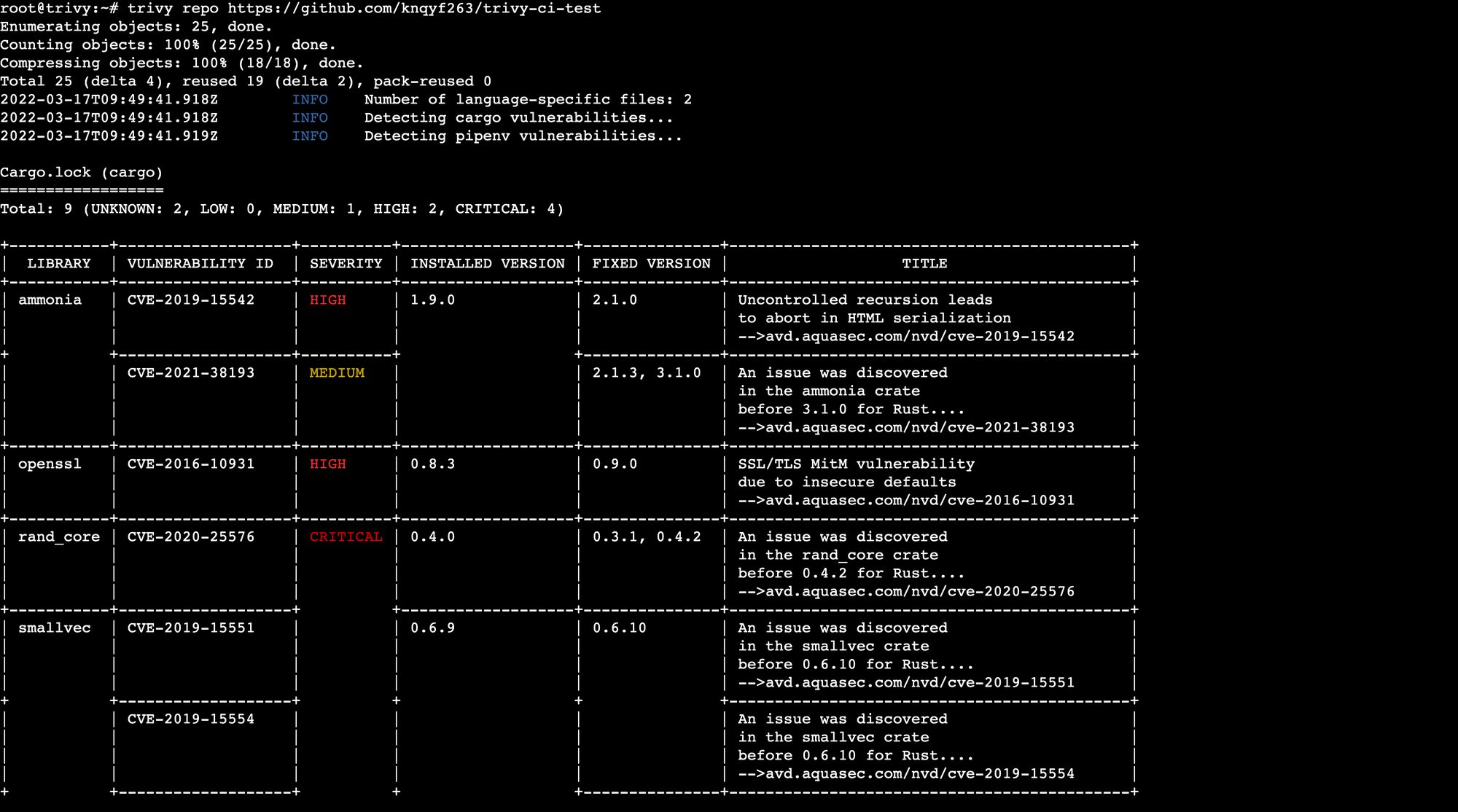
trivy repo [REMOTE_REPO_URL]Sample (truncated) results of a vulnerability scan on the trivy-ci-test git repository are shown below.
To scan a private GitHub or GitLab repository, you'll need to set the GITHUB_TOKEN or GITLAB_TOKEN environment variable respectively with a valid token that has access to the repository. For example:
export GITHUB_TOKEN=<GITHUB_TOKEN>
trivy repo [PRIVATE_REPO_URL]Scan IaC Config File for Misconfigurations
To scan a directory containing infrastructure-as-code (IaC) config files, run the following command. Trivy supports Terraform, AWS CloudFormation, Dockerfile and Kubernetes config files.
trivy config [IaC_DIRECTORY]Sample (truncated) results of a misconfiguration scan on the trivy/examples/misconf/mixed git repository are shown below.
git clone https://github.com/aquasecurity/trivy
cd trivy/examples/misconf/mixed/
trivy config configs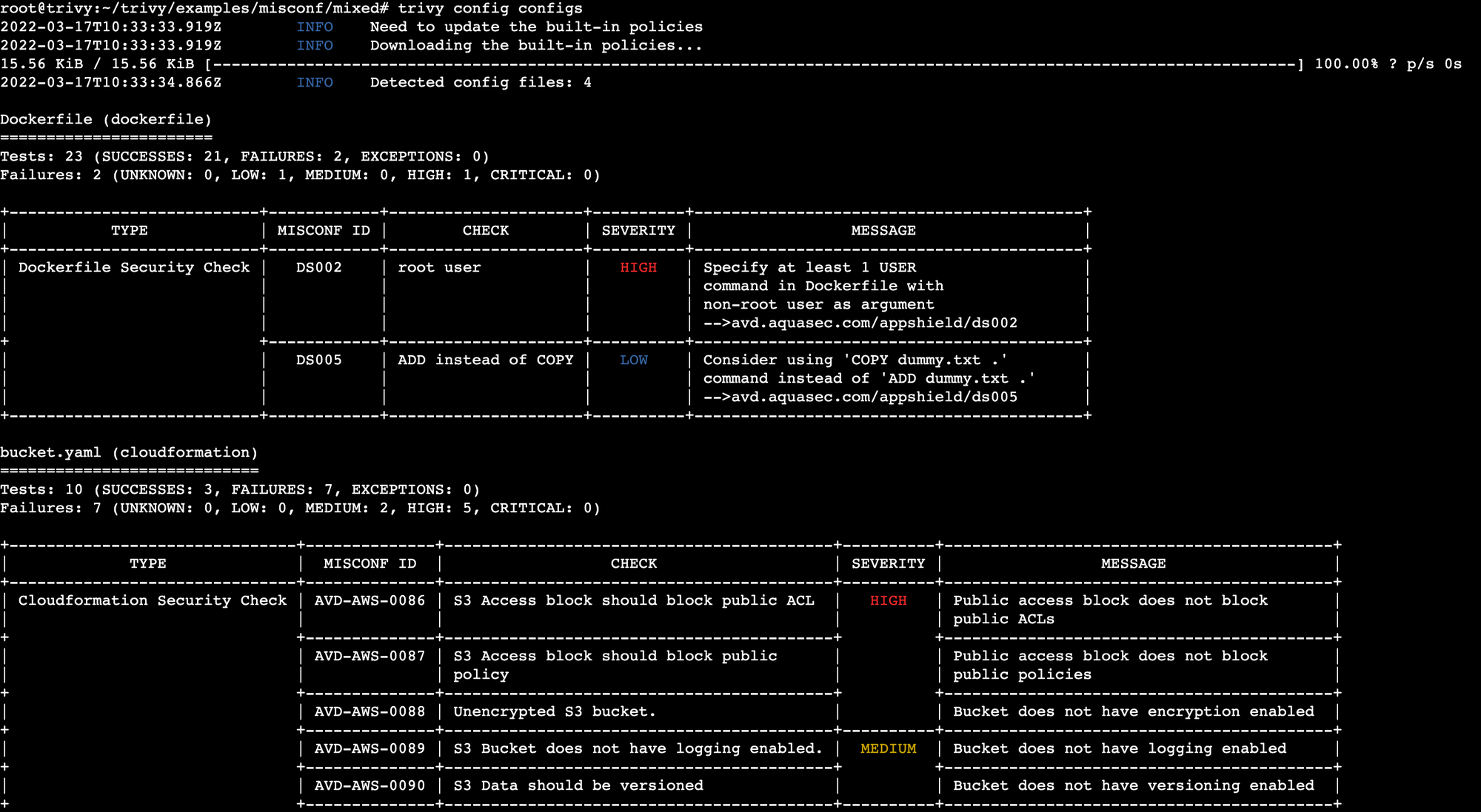
Integrate Trivy with Your CI Pipeline
I'm just scratching the surface here - Trivy is quite powerful and can cover several other use cases. One key use case is integration with continuous integration (CI) pipelines for automated vulnerability scans. Trivy integrates with CI tools like CircleCI and Travis CI, and can also be included in Github workflows with Actions. See this post from Aqua for more details.