Fix Your DNS Security Blind Spot
A brief on Google 8.8.8.8 and Cloudflare 1.1.1.1, two security-focused DNS resolvers.
The Domain Name System (DNS) is one of the fundamental building blocks of the internet. It maps human-readable names to IP addresses for computers, services and other resources connected to the internet. It is essentially a huge phone book.
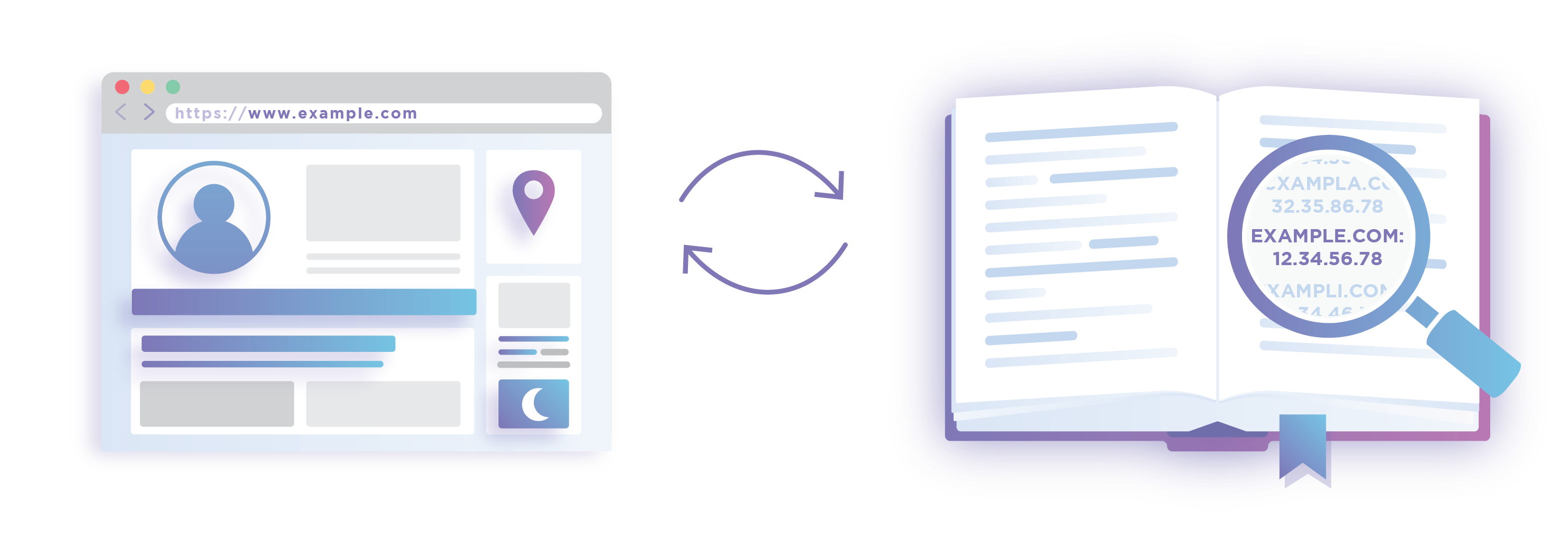
A DNS resolver (or recursive resolver) is a server that retrieves the name-IP mapping from the DNS name server for any device that requests it. Most people use the resolver provided by their Internet Service Provider (ISP) and do not change it. But think about this - the DNS resolver is literally the first entity that learns about each of your web requests. And, irrespective of what happens later in the DNS resolution process, the resolver can build a complete dossier on your web browsing habits. Not only is this a serious concern from a privacy perspective, but also creates a honeypot for attackers if not guarded well.
Poorly secured DNS resolvers are vulnerable to DNS spoofing and forgery attacks. This leads to DNS cache poisoning, which in turn can redirect legitimate traffic to malicious websites hosted by the attackers. Such DNS resolvers are also vulnerable to denial of service (DoS) attacks, or may themselves be the victims of compromise leading to DoS attacks on other servers (known as amplification attacks).
So, what should you do? Easy. Do not use the default DNS servers provided by your ISP. From a security viewpoint, you have two good alternatives - use the public resolvers provided by Google (primary: 8.8.8.8 / secondary: 8.8.4.4) or Cloudflare (primary: 1.1.1.1 / secondary: 1.0.0.1). Both companies are extremely well regarded in the security industry; they offer fast DNS lookups, support advanced DNS security mechanisms like query minimisation, DNSSEC, DNS over TLS (DoT) and DNS over HTTPS (DoH), and store logs up to 24-48 hours only for troubleshooting and security investigations. (Google may store certain anonymised logs longer, but they explain their log sampling policy clearly here).
Depending on your device, the DNS settings may be slightly different, but are fairly straightforward to update. Google provides a guide for different devices here. Hope this post spurs you into fixing your DNS security blind spot today.