3 Tips to Secure Your GCP VM Instance
3 quick and easy tips to secure remote administrative access to your GCP VM instance.
Cloud security is a shared responsibility between between the Cloud Service Provider and the customer. Too often, customers neglect basic security hygiene when configuring the cloud platform or using resources such as virtual machine (VM) instances. Today, I cover three quick and easy tips to secure remote administrative access to your Google Cloud Platform (GCP) VM instances. Tl;dr, you can:
- Verify boot integrity using Shielded VMs
- Manage SSH access using OS Login
- Tunnel SSH/RDP connections using Identity-Aware Proxy (IAP)
To be clear, this is neither an exhaustive list of recommendations nor guaranteed to keep your VM instances secure from an adversary with sufficient motivation and resources. But it will surely shrink the overall attack surface as you consider and implement other security controls.
Verifiable Boot Integrity with Shielded VMs
Shielded VMs are virtual machines on GCP that are hardened by default using a set of boot-time security controls. Shielded VMs leverage advanced platform security capabilities such as secure and measured boot, a virtual trusted platform module (vTPM), UEFI firmware, and integrity monitoring to help defend against rootkits and bootkits. They were the first in a series of Google initiatives to implement shielded computing across the platform, subsequently followed by Shielded GKE Nodes.
Shielded VMs are intentionally easy to configure, enabled by default and do not incur an additional charge, encouraging all organizations to seriously consider using them during VM migration and deployment.
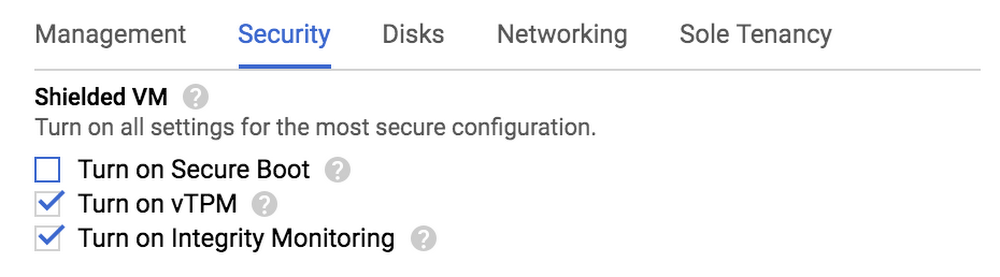
If you want to build upon this, you can set the constraints/compute.requireShieldedVm organization policy constraint to True to require that Compute Engine VM instances created in your organization be Shielded VM instances. And, as a bonus, if you use CIS hardened images as your "base" or "golden" images, they now have Shielded VM features enabled by default.
SSH Access Management with OS Login
OS Login simplifies SSH access management by linking your Linux user account to your Google identity. You can manage SSH access to your instances using IAM without having to create and manage individual SSH keys. If users leave your organization, you can simply disable/delete the user accounts and remove their access from the VM instances without worrying about a proliferation of SSH keys. And because OS Login is tied to IAM, permissions are automatically updated when administrators change IAM permissions.
To configure OS Login and connect to your instances:
- Enable OS Login by setting the metadata
enable-osloginvalue toTRUEat the instance or project level. - Grant
roles/compute.osLogin(no administrator permissions) orroles/compute.osAdminLogin(with administrator permissions) role to the user (group recommended). - If your VM instance uses a service account, then the user must also have the
roles/iam.serviceAccountUserrole on the service account.
As with Shielded VMs, you can set the constraints/compute.requireOsLogin organization policy constraint to True to require that OS Login is enabled by default on all VM instances in new projects.
If you want to enhance OS Login by using two-factor authentication, see Setting up OS Login with 2-step verification.
SSH/RDP Tunneling with Identity-Aware Proxy (IAP)
IAP TCP forwarding allows you to establish an encrypted HTTPS tunnel over which you can forward SSH, RDP, and other TCP traffic to VM instances. This effectively adds a coarse-grained authorization layer and eliminates the need for your VMs to be publicly exposed on the internet. This feature is meant to secure administrative access though and not to be used as a data transfer mechanism.
As depicted below, IAP creates a listening port on the local host that forwards TCP traffic to the specified instance, wrapped in an HTTPS connection. Enabling IAP does not automatically block direct requests to the resource though, only requests that aren't from IAP TCP forwarding IPs to relevant services on the resource.
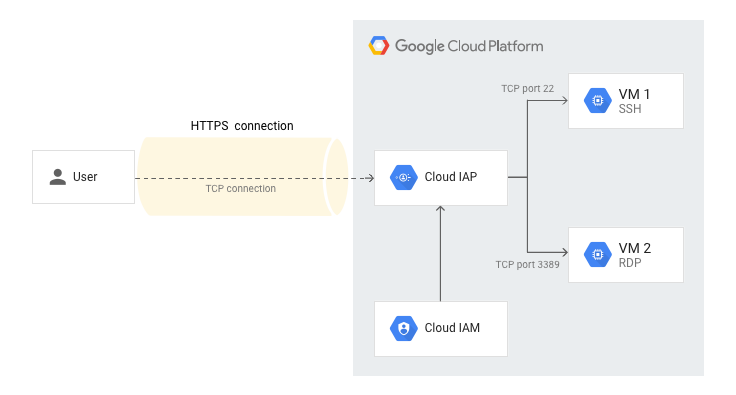
To set up SSH/RDP forwarding via IAP for your VM instance:
- Create a firewall rule
allow-ssh-from-iapthat allows ingress traffic from IP range35.235.240.0/20on TCP port22. - Create a firewall rule
allow-rdp-from-iapthat allows ingress traffic from IP range35.235.240.0/20on TCP port3389. - Navigate to
Security>Identity-Aware Proxy. From the SSH and TCP resources page, select the VM instance you want to configure. - Click
Show info paneland grantCloud IAP>IAP-Secured Tunnel Userrole to the desired user (group recommended). - See Tunneling SSH connections for remote SSH access.
- See Tunneling RDP connections for remote RDP access.
- You can also tunnel other TCP connections by setting up a local port that tunnels TCP traffic over HTTPS to the remote instance.
Well, there you have it - three quick and easy tips to secure remote administrative access to your GCP VM instances. For additional security best practices, see here and here.