What is Business Email Compromise?
A brief on business email compromise, a common scam targeting individuals and businesses.
According to the latest public service announcement from FBI, there was a 65% increase in identified global exposed losses related to business email compromise/email account compromise (BEC/EAC) between July 2019 and December 2021, with total losses since July 2016 exceeding $43 billion. And this was exacerbated since the advent of Covid-19, with more business being conducted online than ever before. So, what is BEC/EAC, why is it a concern, and what can you do about it?
To understand BEC, we need to understand email phishing first. Phishing is a social engineering attack technique that employs malware or deception to elicit sensitive information from the victim. While phishing is observed with voice, SMS and other communications media too, email is by far the most exploited medium, with over 90% of all data breaches originating from an email phishing attack.
Business email compromise (BEC) is a targeted email phishing attack that tricks unsuspecting victims into making fund transfers to unintended recipients. The fraudsters carefully research victim organisations via LinkedIn and other forums, understand personnel roles and reporting hierarchies, and impersonate executives typically authorised to make the fund transfers. The emails also employ a tone of urgency and directness (or helplessness) to manipulate the victims into action. Once the transfer completes, the funds are often routed through shadow accounts or converted to cryptocurrency, making recovery efforts hard.
According to the FBI, there are 5 types of BEC scams: false invoice scheme, CEO fraud, account compromise, attorney impersonation and data theft. BEC attacks are difficult to detect because they don't use malicious attachments or links; they rely on impersonation and emotional appeal to trick victims into compliance.
Email Account Compromise (EAC) is a close variant of BEC, where the attacker targets and gains control over a legitimate email account, often an executive. If the account compromise is not detected, subsequent EAC attacks are quite challenging to thwart as emails to the victims are actually from a legitimate source.
Now that you understand the mechanics of BEC/EAC scams, here are some things you can consider to avoid becoming a victim:
- Your users are the target; raise security awareness across your organisation. Run periodic phishing simulation drills to reinforce best practices.
- Deploy email phishing protection software; some have pretty decent BEC detection too. Popular SaaS-based email services like Google Workspace and Microsoft Office 365 include phishing protection in their premium tiers.
- Consider using products/services that clearly label external emails/senders (e.g. Google Workspace).
- If not using SaaS-based email services, ensure that the email infrastructure (e.g. Exchange servers) has latest patches and malware protections installed.
- Ensure that two-factor authentication is configured for all users. If possible, use hardware security keys like Google Titan or Yubikey (USB-A/NFC, USB-C/NFC or USB-C/Lightning).
- Verify the complete email address of the sender (including domain name), not just the display name. Same with links. Take extra care on a mobile device.
- Payments/remittances should be made to the same account used previously. If this is the first transaction, verify the account details via a phone call or text message to the recipient.
- Send a smaller amount and verify receipt before initiating a large transfer.
- If you have a well-established process (e.g. workflow via accounting software), beware of any request that tries to bypass the process.
- Finally, urgency is one of the most effective tactics in a social engineer’s toolkit. Resist the temptation to respond urgently. Trust your intuition.
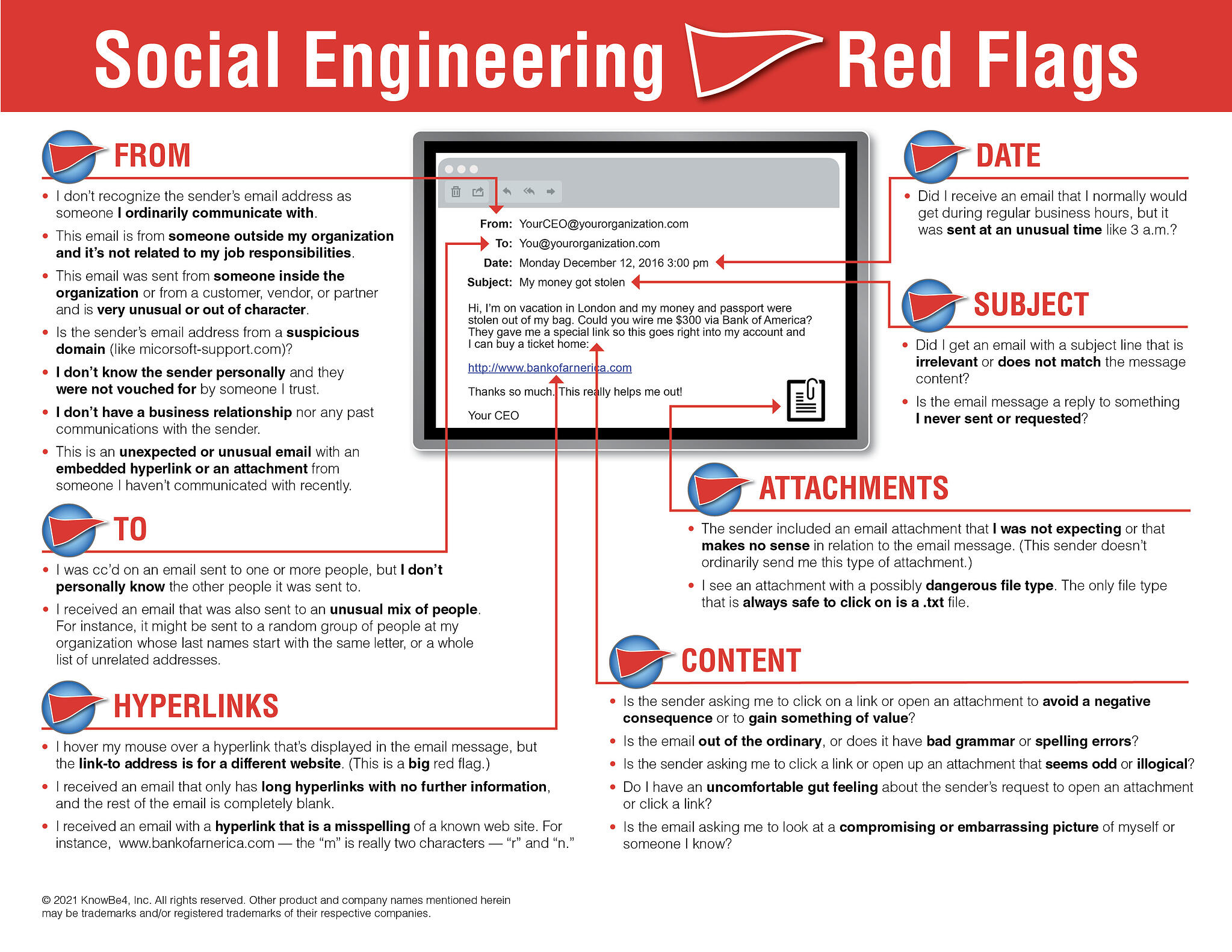
In addition to my recommendations, here is an excellent KnowBe4 infographic outlining several red flags to look for when you receive suspicious emails.