Practice Hacking Skills with OWASP Juice Shop
Practice your hacking skills with the OWASP Juice Shop, a modern yet insecure web application.
If you are just starting in web application security, you should be familiar with different types of attacks that occur against web applications, and keep abreast of the latest security techniques, tools and trends. But you also need to practice what you learn, and sharpen existing skills, against vulnerable web applications. Some popular examples include WebGoat, Metasploitable, DVWA, Goof, Gruyere, and Juice Shop. If you are keen to explore more, OWASP has published a comprehensive list at the Vulnerable Web Applications Directory.
What is OWASP Juice Shop?
OWASP Juice Shop is an intentionally vulnerable web application that allows security enthusiasts to test their skills. It is designed to help developers and security professionals better understand the risks and techniques associated with web application attacks. It can be used in security trainings, awareness demos, capture-the-flag events, testing security tools, and honing your web application hacking skills. It covers vulnerabilities from the highly popular OWASP Top Ten list, and also includes some flaws found in real-world applications. The 100+ vulnerabilities can be categorised as follows (source: OWASP Juice Shop).
| Category | # | Challenges |
|---|---|---|
| Broken Access Control | 10 | Admin Section, CSRF, Easter Egg, Five-Star Feedback, Forged Feedback, Forged Review, Manipulate Basket, Product Tampering, SSRF, View Basket |
| Broken Anti Automation | 4 | CAPTCHA Bypass, Extra Language, Multiple Likes, Reset Morty's Password |
| Broken Authentication | 9 | Bjoern's Favorite Pet, Change Bender's Password, GDPR Data Erasure, Login Bjoern, Password Strength, Reset Bender's Password, Reset Bjoern's Password, Reset Jim's Password, Two Factor Authentication |
| Cryptographic Issues | 5 | Forged Coupon, Imaginary Challenge, Nested Easter Egg, Premium Paywall, Weird Crypto |
| Improper Input Validation | 10 | Admin Registration, Deluxe Fraud, Expired Coupon, Missing Encoding, Payback Time, Poison Null Byte, Repetitive Registration, Upload Size, Upload Type, Zero Stars |
| Injection | 11 | Christmas Special, Database Schema, Ephemeral Accountant, Login Admin, Login Bender, Login Jim, NoSQL DoS, NoSQL Exfiltration, NoSQL Manipulation, SSTi, User Credentials |
| Insecure Deserialization | 2 | Blocked RCE DoS, Successful RCE DoS |
| Miscellaneous | 5 | Bully Chatbot, Mass Dispel, Privacy Policy, Score Board, Security Policy |
| Security Misconfiguration | 4 | Cross-Site Imaging, Deprecated Interface, Error Handling, Login Support Team |
| Security through Obscurity | 3 | Blockchain Hype, Privacy Policy Inspection, Steganography |
| Sensitive Data Exposure | 16 | Access Log, Confidential Document, Email Leak, Exposed Metrics, Forgotten Developer Backup, Forgotten Sales Backup, GDPR Data Theft, Leaked Access Logs, Leaked Unsafe Product, Login Amy, Login MC SafeSearch, Meta Geo Stalking, Misplaced Signature File, Reset Uvogin's Password, Retrieve Blueprint, Visual Geo Stalking |
| Unvalidated Redirects | 2 | Allowlist Bypass, Outdated Allowlist |
| Vulnerable Components | 9 | Arbitrary File Write, Forged Signed JWT, Frontend Typosquatting, Kill Chatbot, Legacy Typosquatting, Local File Read, Supply Chain Attack, Unsigned JWT, Vulnerable Library |
| XSS | 9 | API-only XSS, Bonus Payload, CSP Bypass, Client-side XSS Protection, DOM XSS, HTTP-Header XSS, Reflected XSS, Server-side XSS Protection, Video XSS |
| XXE | 2 | XXE Data Access, XXE DoS |
What is Railway?
Railway is a modern app hosting platform that makes it easy to deploy production-ready apps quickly. Railway offers persistent database services for PostgreSQL, MySQL, MongoDB, and Redis, as well as application services with a GitHub repository as the deployment source. For the latter, Railway can automatically determine the application runtime and deploy the service. We'll use this approach to deploy OWASP Juice Shop - if you want to wipe your progress and start over, simply redeploy the service. Since we are just testing the waters, Railway's free tier should be sufficient to host the service.
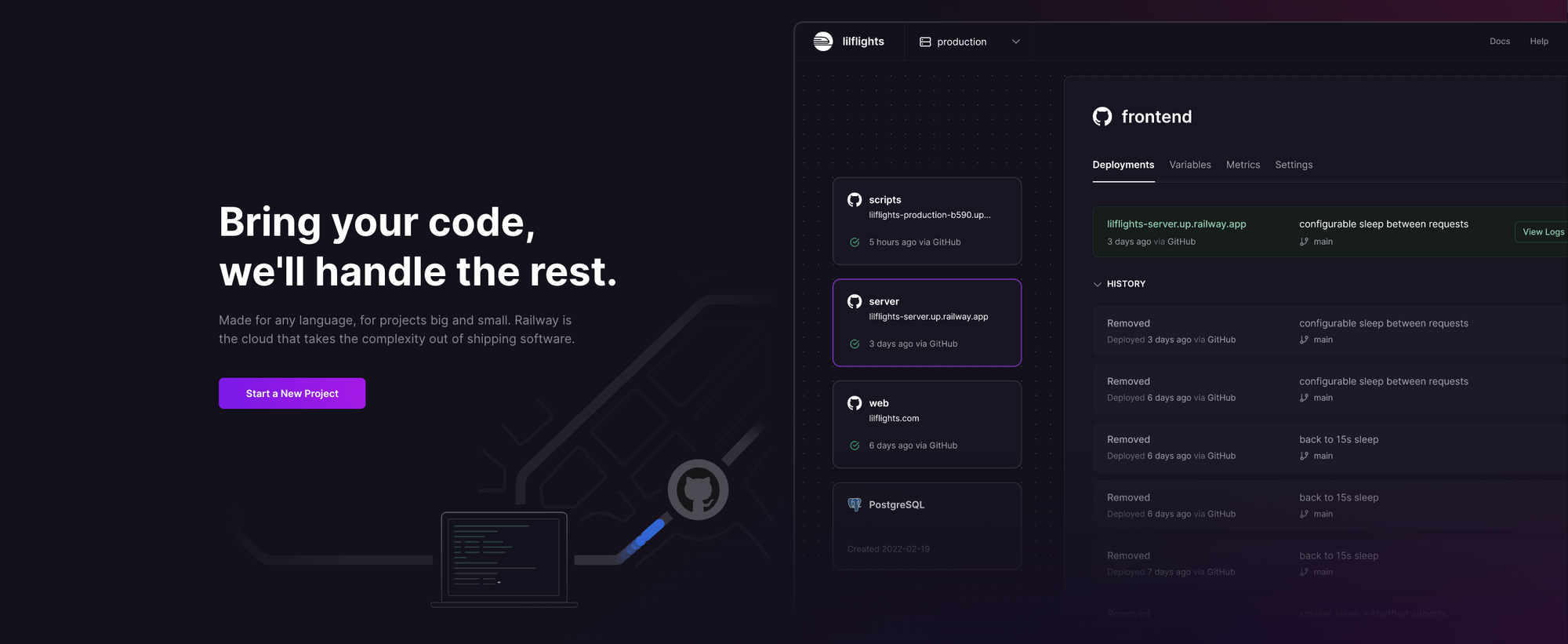
Deploy OWASP Juice Shop on Railway
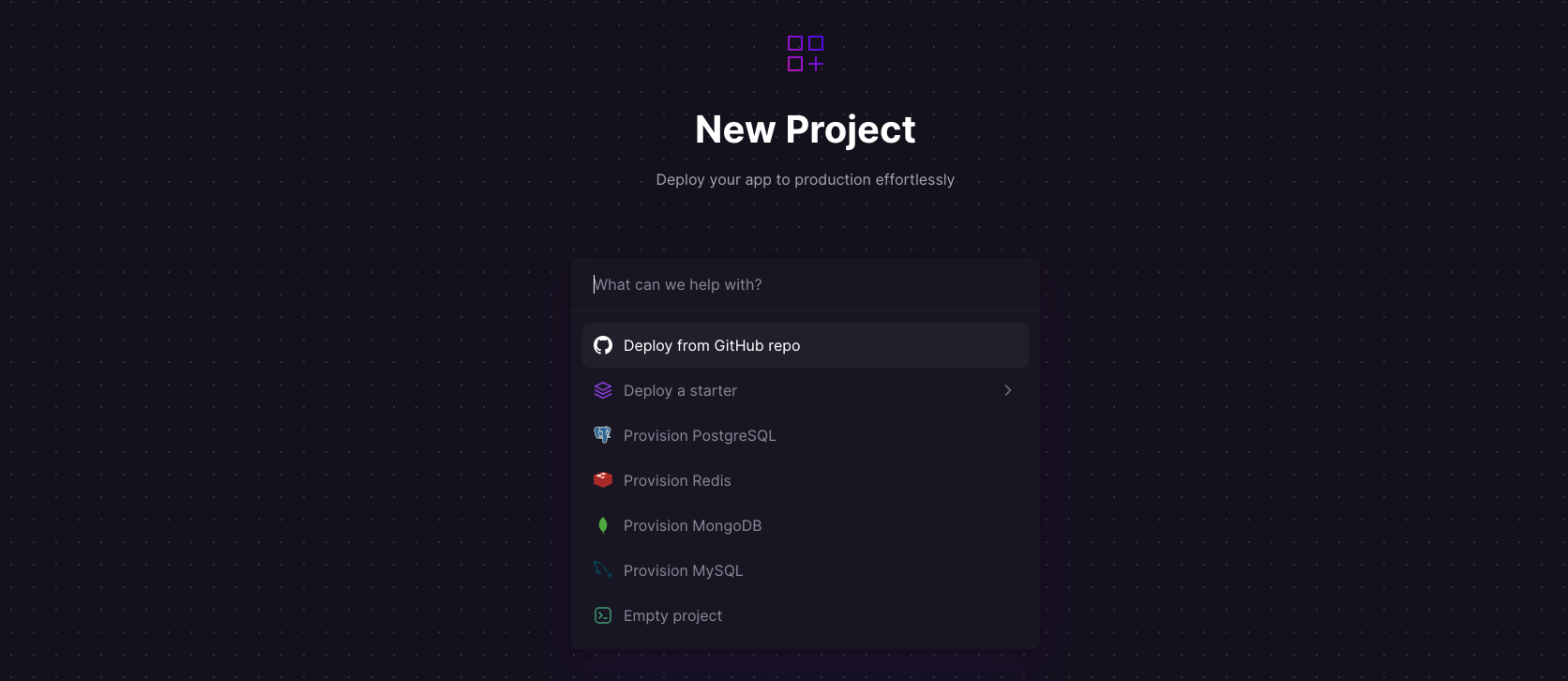
Log into your GitHub account, and fork the Juice Shop repository. Sign up for an account with Railway using GitHub, and click Authorize Railway App when redirected. Review and agree to Railway's Terms of Service and Fair Use Policy if prompted. Click on + New Project > Deploy from GitHub repo, and select your repository. The deployment will kick off immediately. You can also use the OWASP Juice Shop one-click starter template (or click the button below) to deploy the app instantly on Railway.
Once the deployment completes, go to Settings > Domains and click Generate domain to expose the service to the public internet - you'll get a default xxx.up.railway.app domain. Click on this URL to access your OWASP Juice Shop instance. If you are interested in setting up a custom domain, I covered it at length in a previous post - see the final section here.
Practice Your Hacking Skills
The good folks at Juice Shop have done a phenomenal job in creating a companion guide at Pwning OWASP Juice Shop, so I won't regurgitate the steps to get started, but I'll just cover a few things that stood out to me:
- The project is actively maintained, and heavily used, unlike a lot of similar projects attempted in the past.
- It has great documentation and an active community forum.
- While it cannot handle a large DDoS attack, it can withstand typical hacking attempts during security testing, and can be easily redeployed using the self-healing feature.
- It has a well-developed and easy-to-use challenge tracking system, with increasing difficult levels for the challenges.
- It works well with different browsers, scripts/plugins and penetration testing tools.
- It can be used for capture-the-flag style events with popular open source frameworks or game servers (CTFd, FBCTF, RootTheBox).
- It can be customised to match internal brand/application look-and-feel.