Enable Security Keys with OS Login for GCP VMs
A brief on enabling security keys for remote SSH access with OS Login for GCP VMs.
With the release of OpenSSH 8.2, FIDO authentication was natively supported in SSH. Riding on this capability, Google just announced that FIDO security keys can now be used to authenticate to Google Compute Engine (GCE) virtual machines (VMs) that use OS Login for SSH management. This feature is a great complement to the 3 remote access security controls that I've covered in the past.
What are FIDO Security Keys?
Instead of storing the SSH private keys insecurely on your laptop, you can protect the keys using purpose-built FIDO hardware like Google Titan or Yubikey. Depending on your laptop/phone hardware, you may require a different Yubikey version - Yubikey 5 NFC for USB-A/NFC, Yubikey 5C NFC for USB-C/NFC or Yubikey 5Ci for dual USB-C/Lightning support. Whichever option you choose, I highly recommend that you set up at least two keys for your account as a backup.
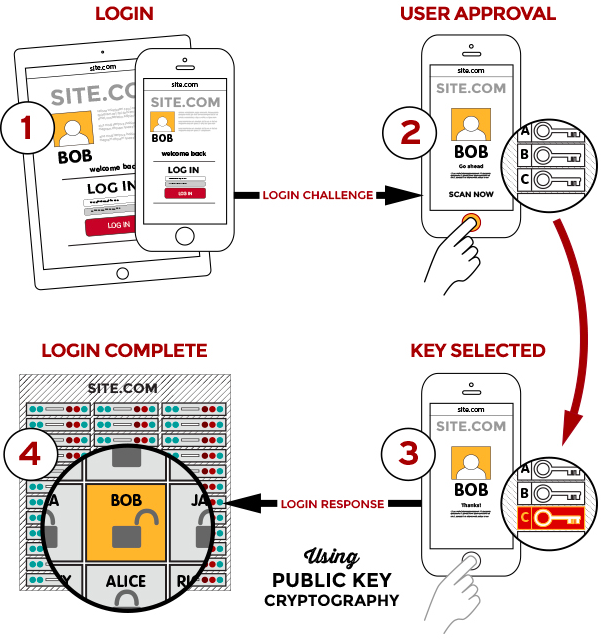
FIDO uses standard public-key cryptography techniques. During registration with a new service, the device creates a new public-private key pair. It stores the private key on the device itself, and registers the public key with the service. For each authentication request, the device unlocks the private key and signs a challenge after a user trigger like a finger swipe or a key press. Biometric information can also be used and is always stored locally, just like the private keys.
Enable Security Keys with OS Login
OS Login simplifies SSH access management by linking your Linux user account to your Google identity. You can manage SSH access to your instances using IAM without having to create and manage individual SSH keys. If users leave your organization, you can simply disable/delete the user accounts and remove their access from the VM instances without worrying about a proliferation of SSH keys.
To configure OS Login and connect to your instances using a security key:
- Add a security key to your Google Account.
- Enable OS Login by setting the metadata
enable-osloginvalue toTRUEat the instance or project level. - Enable support for security keys by setting the metadata
enable-oslogin-skvalue toTRUEat the same level. - Grant
roles/compute.osLogin(no administrator permissions) orroles/compute.osAdminLogin(with administrator permissions) role to the user (group recommended).
To connect to the VM, use a terminal with gcloud tools installed and run: gcloud beta compute ssh <vm_name>.
This feature just released in preview, and has a few limitations at the moment:
- It supports user accounts only; service accounts connect without security keys
- VMs with security keys enabled can't use the GCP Console-based SSH tool
- To check if your Linux environment supports security keys, run:
ssh -Q key | grep ^sk-
Once you enable security key support through OS Login, you can use any of the keys configured on your Google account during login. The security keys can also be combined with another authentication factor for two-step verification (2SV), adding an extra layer of security (see Setting up OS Login with 2-step verification).