Detect Leaked Secrets with TruffleHog
A brief guide on detecting leaked secrets using open-source Trufflehog.
Committing secrets to GitHub along with your source code is a good idea. Not!
In recent years, we've seen plenty of media reports where developers inadvertently committed secrets to git repositories. Whether due to lack of education, negligence or just mistakes, the outcomes were often catastrophic for their organisations. According to a recent study by Argon Security, software supply chain attacks more than tripled in 2021, and lack of code/artefact integrity due to exposed secrets in code was one of the main risks contributing to it. Secret leakage is also #2 on the OWASP Top 10:2021 list of weaknesses (A02 Cryptographic Failures, previously called Sensitive Data Exposure). In this post, we'll look at an easy way to detect secrets hidden in your git repositories and other files.
What is TruffleHog?
TruffleHog is an open-source tool that scans your environment for secrets like SSH private keys, API keys, database passwords, authentication/access tokens, cloud credentials and more. It can run scans continuously in the background every time changes are made and notify you when secrets are found. TruffleHog v3 is a complete rewrite in Go, making the tool faster and more useful with 600+ secret type detectors and automatic validation against the respective APIs.
Truffle Security, the company behind TruffleHog, also published Driftwood, another open-source tool which takes an asymmetric private key, extracts the corresponding public key, and compares the latter against an internal database of known exposed public keys. Combined with TruffleHog, Driftwood offers visibility into your overall exposure and is a useful tool to have in your security arsenal.
Deploy TruffleHog on a DigitalOcean Droplet
I'll use DigitalOcean for this brief - if you don't have an account, sign up here. If you use this link, you’ll get a $200, 60-day credit when you add a valid payment method to your account. Set up your team and project, and create a basic droplet. Without really going into details, choose a plan (2GB RAM / 1 CPU), an image (Ubuntu 20.04), the data center region, an authentication option (root password for now, but non-root user in a real environment) and the hostname.
Once the droplet is ready, select it and launch the Droplet Console as root from the menu options. Run the following commands to update the Ubuntu instance, install Python dependencies and the TruffleHog package.
# Update the package metadata and packages to the latest versions
apt update && apt upgrade
# Install Python 3 supporting packages; Python should already be present
apt install -y --no-install-recommends python3-virtualenv
# Create a Python virtual environment, install pip and TruffleHog
python3 -m virtualenv --python=/usr/bin/python3 .env
source .env/bin/activate
python3 -m pip install -U pip virtualenv
pip install trufflehogScan Your Git Repositories for Secrets
To scan your git repositories, simply run the following command.
# Replace GIT_REPO_URL with your git repository URL
trufflehog GIT_REPO_URLSample (truncated) results of a secrets scan against a test repo are shown below.
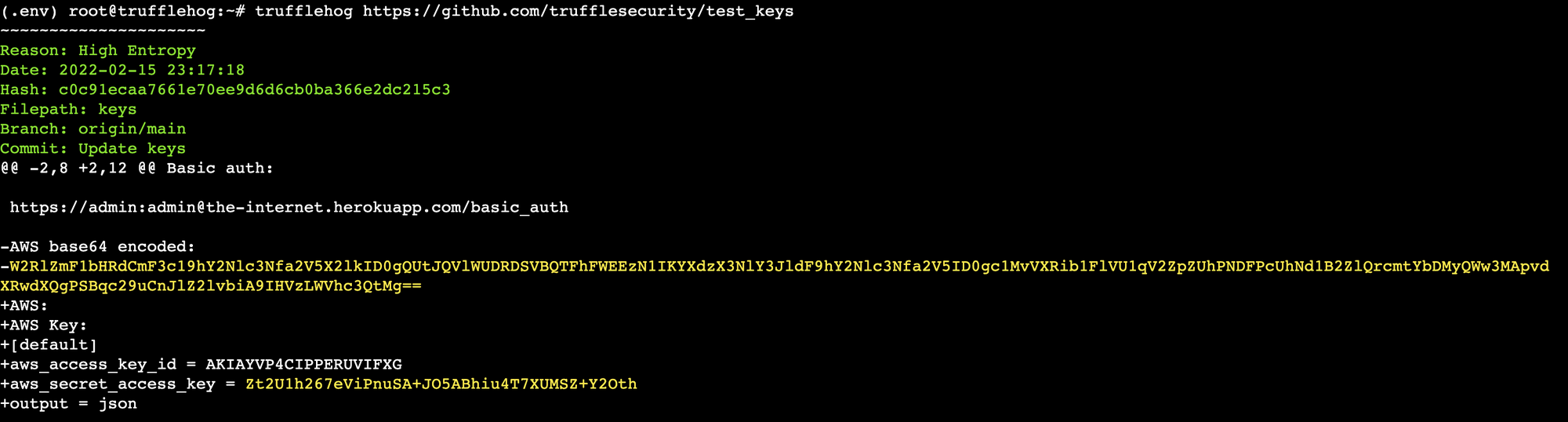
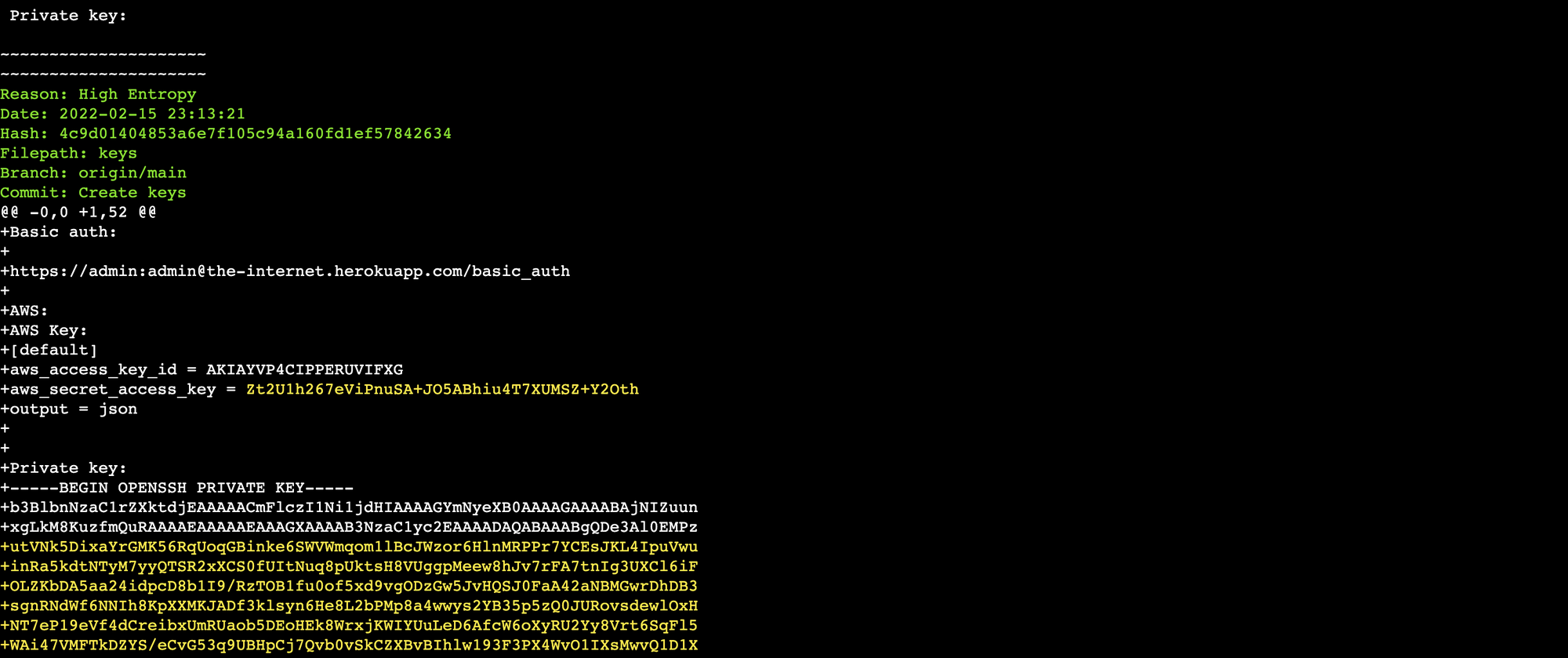
Here are a few useful flags (see Github for the complete list):
--helpcontext-sensitive help--jsonget output in JSON format--only-verifiedonly show verified results--include-paths=INCLUDE-PATHSpaths to include in scan--exclude-paths=EXCLUDE-PATHSpaths to exclude in scan--branch=BRANCHbranch to scan
If you prefer to run TruffleHog as a Docker container, skip the Python commands in the previous section and run the following instead.
# Install the Docker package
apt install docker.io
# Replace GIT_REPO_URL with your git repository
docker run -it -v "$PWD:/pwd" trufflesecurity/trufflehog:latest GIT_REPO_URLSample (truncated) results of a secrets scan against a test repo are shown below.
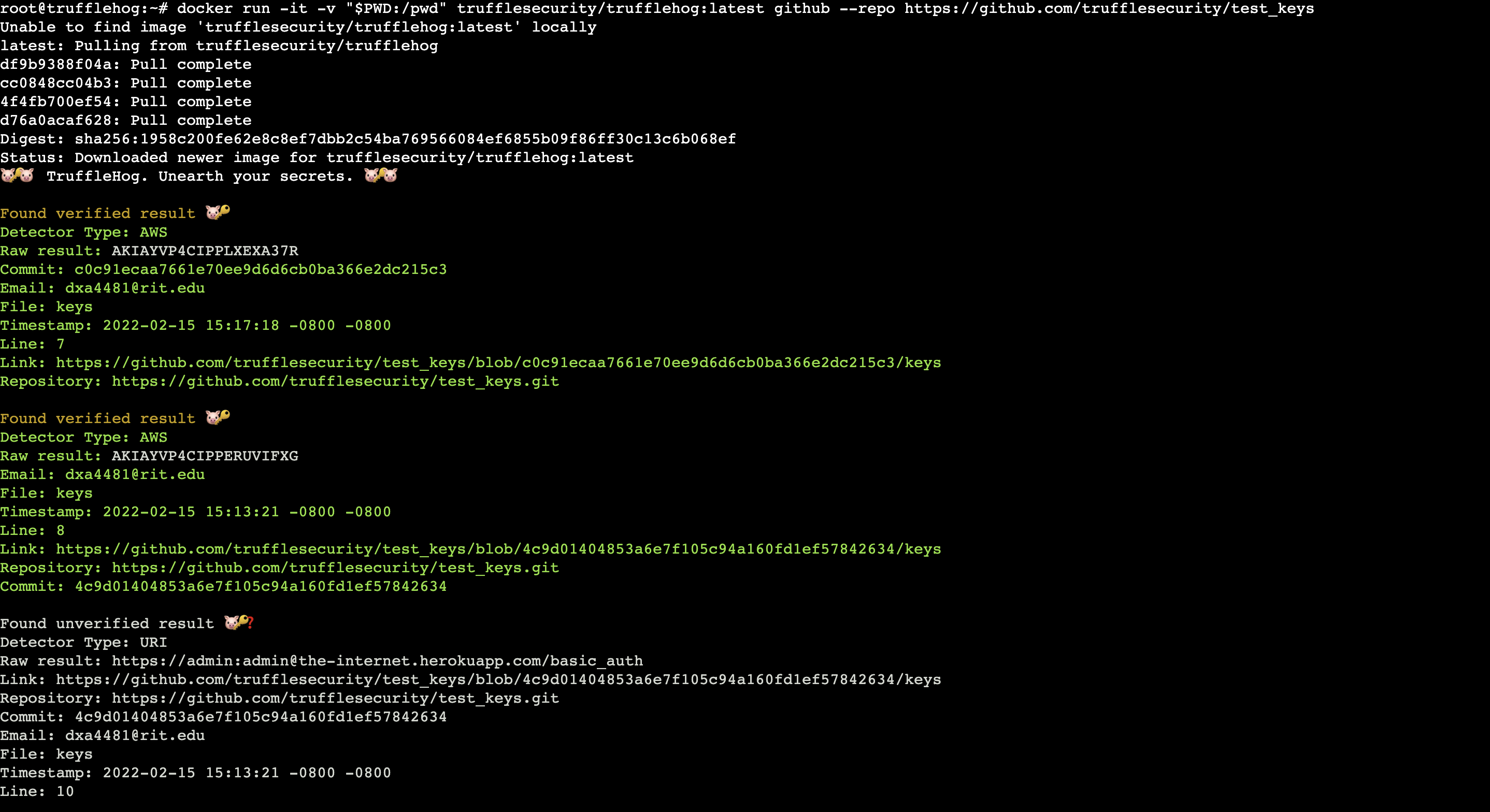
Hackers are already having a field day with platform misconfigurations and application vulnerabilities. Don't make it easier by leaking secrets.