Cloud Security Posture Assessment with Scout Suite
A brief on cloud security posture assessment for Google Cloud with Scout Suite.
While hyperscaler platforms like AWS, Azure and Google Cloud are investing billions to secure the underlying cloud infrastructure, cloud customers are still struggling to secure their applications and services. Not a week goes by without a headline-grabbing data breach or leakage from an avoidable misconfiguration. In fact, according to a recent IDC study, 98% of the surveyed organizations reported having at least one cloud data breach in the previous 18 months!
To tackle this problem, the hyperscalers and other security vendors offer CSPM (Cloud Security Posture Management) tools and capabilities to proactively and reactively identify and remediate security risks. However, commercial offerings may not always be affordable for customers just starting out with cloud, despite security being a top priority. Thankfully, there are a few open-source tools addressing this space. In a previous post, I covered CloudSploit by Aqua. Today, I'll explore Scout Suite by the NCC Group.
What is Scout Suite?
Scout Suite is an open-source cloud infrastructure security auditing tool. It officially supports AWS, Azure and Google Cloud, with support for Alibaba Cloud and Oracle Cloud Infrastructure in alpha. It uses APIs provided by the hyperscalers to gather configuration data from cloud environments, and runs manual inspections against the data. For this walk-through, we'll run the scans against Google Cloud assets.

Set up the Scout Suite Service Account
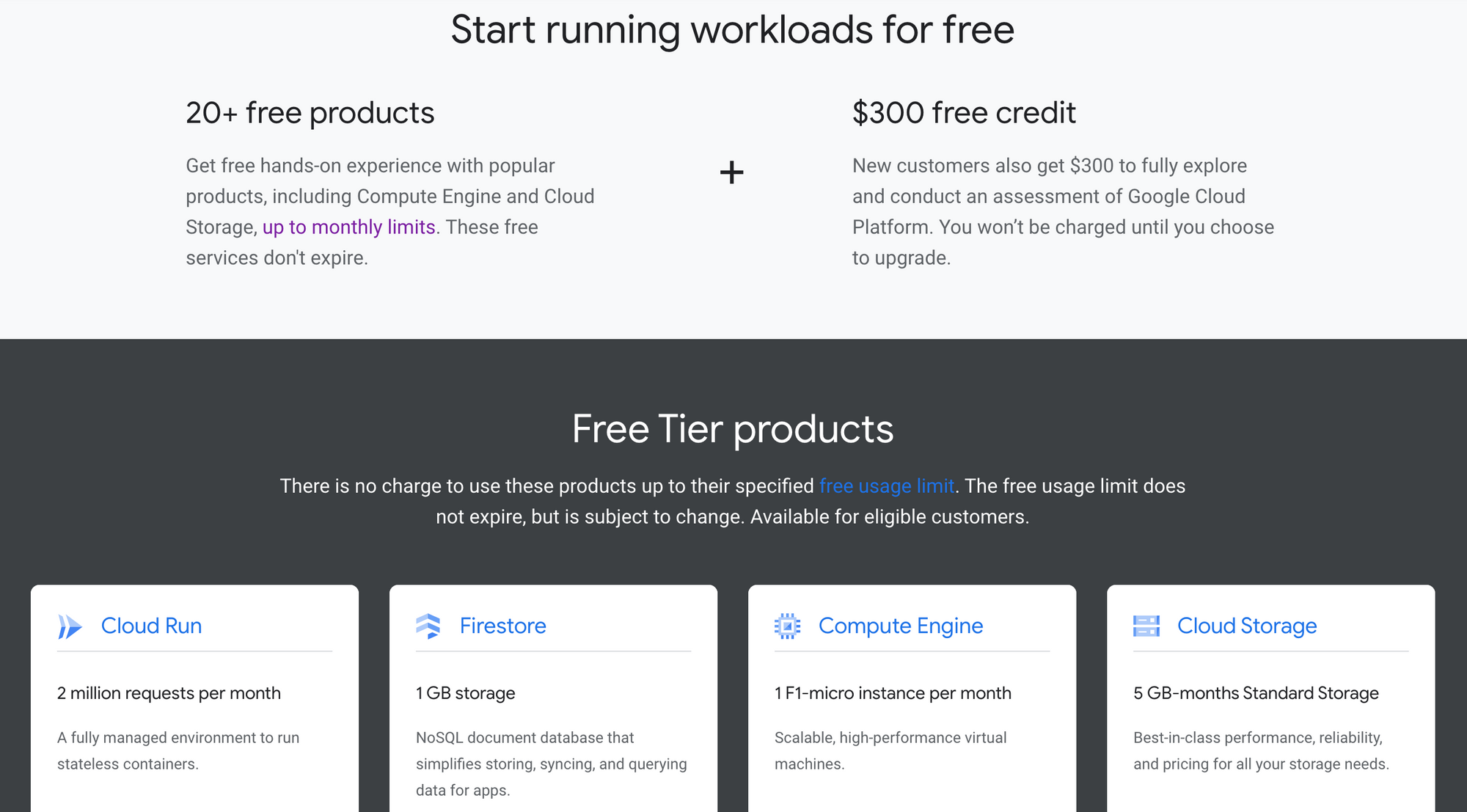
I'm assuming that you already have a Google Cloud account and project set up. If you don't, sign up here - new customers get a generous $300 credit for 90 days, with several always-free products once the trial period expires.
Scout Suite can be executed either in the context of the user running the CLI commands or a non-interactive service account created solely for such scans. Use the -u or --user-account flag for users, and -s or --service-account flag for service accounts. Let's create a service account with view-only privileges to the Google Cloud project you want to assess. You can run Scout Suite at a folder or organization level too if you wish - create and grant privileges to the service account accordingly.
Enable billing on your account, create a new project, and follow the steps below.
- Launch Google Cloud Console and navigate to
IAM & Admin>Service Accounts. - Click on
Create Service Accountoption. Service account details:
a.Service account name: Scout Suite
b.Service account ID: <default>
c.Service account description: Scout Suite API Access - Click
Create and Continue. - Grant this service account access to the project:
a.Role>Basic>Viewer.
b.Role>IAM>Security Reviewer.
c.Role>Cloud Storage>Storage Object Creator. (optional, to copy files over to GCS) - Click
ContinueandDone. - Click on the newly created service account and navigate to
Keystab.
a. Click onAdd Keydropdown and selectCreate new key.
b. Choose default JSON option and clickCreate.
c. Move the JSON file to a secure location. - Scout Suite utilizes the following APIs to run scans, but does not necessarily need all of them to be enabled.
a.Cloud DNS API
b.Cloud Logging API
c.Cloud Monitoring API
d.Compute Engine API
e.Cloud Key Management Service (KMS) API
f.Cloud SQL Admin API
g.Kubernetes Engine API
h.Service Management API
i.Service Networking API
j.Cloud Resource Manager API
k.Identity and Access Management (IAM) API
l.IAM Service Account Credentials API
m.Cloud Memorystore for Memcached API
n.Google Cloud Memorystore for Redis API
o.Cloud Storage API
Install Scout Suite on Google Cloud
Now, let us install Scout Suite on a Google Cloud virtual machine (VM). If you are just exploring, you could deploy Scout Suite on your workstation too.
- If you've just created the trial account, you should have a
defaultVPC network and the corresponding sub-networks for each region already created. If you're using an account that restricts default network creation, go toVPC network>VPC networksand create a VPC network and sub-network first. - Delete the default firewall rules, except
default-allow-ssh, fromVPC network>Firewall. If you prefer not to expose the SSH port to the internet, follow my guidance to tunnel SSH traffic through IAP instead. - Create a new VM instance from
Compute Engine>VM instances. Enter the VM name (say,scoutsuite), select yourregionandzone, choosee2-small (2 vCPU, 2 GB memory)machine type from theGeneral-Purposemachine family, and change the boot disk toUbuntu 20.04 LTS. UnderIdentity and API access>Service accounts, change the assigned service from the default to the previously createdScout Suiteaccount. UnderManagement>Metadata, addenable-osloginandTRUEas a key-value pair. Leave other options as default and clickCreate. - Allow a few seconds for the VM instance to get created. If you followed my IAP guidance above, there should be no public IP address for this instance. In this case, you may need to configure a Cloud NAT gateway to pull updates from the internet.
Once the VM instance is ready, install the latest stable Scout Suite release. SSH into the instance using the browser-based SSH option in Google Cloud console (or your preferred SSH client) and run the following commands. By default, Google Cloud VMs have Python 3.8 and gcloud CLI packages pre-installed.
# Update the package metadata to the latest version
sudo apt update && sudo apt upgrade
# Install Python virtual environment
sudo apt install python3-virtualenv
# Create a Python virtual env and install Scout Suite via pip
virtualenv -p python3 venv
source venv/bin/activate
pip install scoutsuite
# For Google Cloud, review the Scout Suite commands available
scout gcp -hRun a Cloud Security Scan
To run a scan in the context of the logged-in user account, run the following commands. Authorize the user access request in your browser to continue.
- For a specific project:
scout gcp -u --project-id <PROJECT_ID> - For a specific folder:
scout gcp -u --folder-id <FOLDER_ID> - For the entire organization:
scout gcp -u --organization-id <ORGANIZATION_ID> - For all projects that the user has access to:
scout gcp -u --all-projects
To run a scan in the context of the previously created service account, use -s <SA_KEY_FILE.json> instead of the -u flag.
If the requisite Google Cloud APIs have been enabled, and the user/service account has the necessary permissions, the scan will execute and complete shortly. You may see some errors for services that are not being used, but you can ignore those. The scan results will be stored under the scoutsuite-report folder.
If you ran the scan on your local workstation, you can simply launch the gcp-<PROJECT_ID>.html file in your browser to view the results. If you used a Google Cloud VM, you'll need to copy/move the scan results to a different location. I used Google Cloud Storage as a hop between the VM and my workstation.
# Run the following on the Google Cloud VM (assuming bucket exists)
gsutil cp -r scoutsuite-report gs://<bucket-name>
# Run the following on your workstation (assuming you have gcloud)
gsutil cp -r gs://<bucket-name> DownloadsView Scout Suite Results
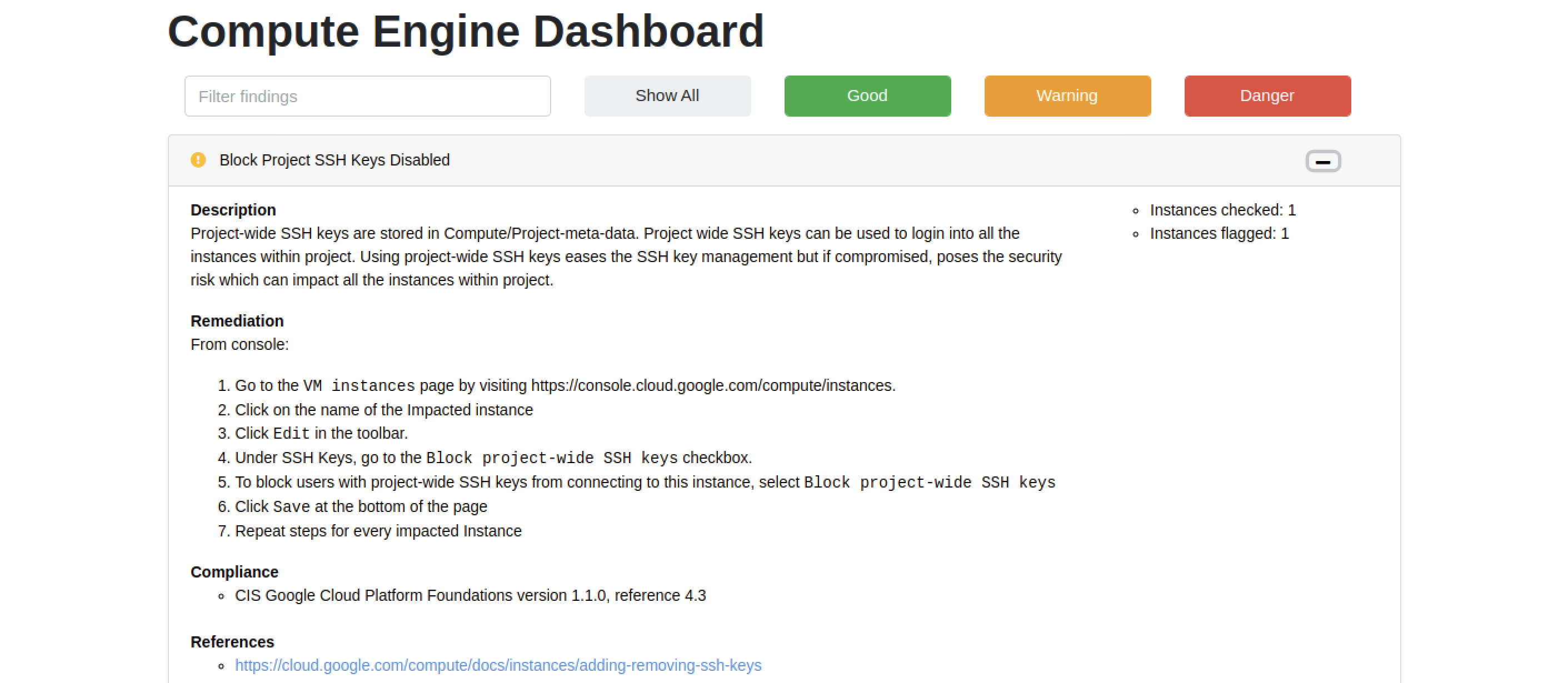
Scout Suite offers a neatly formatted summary dashboard, with a drill down into different categories and the individual findings.
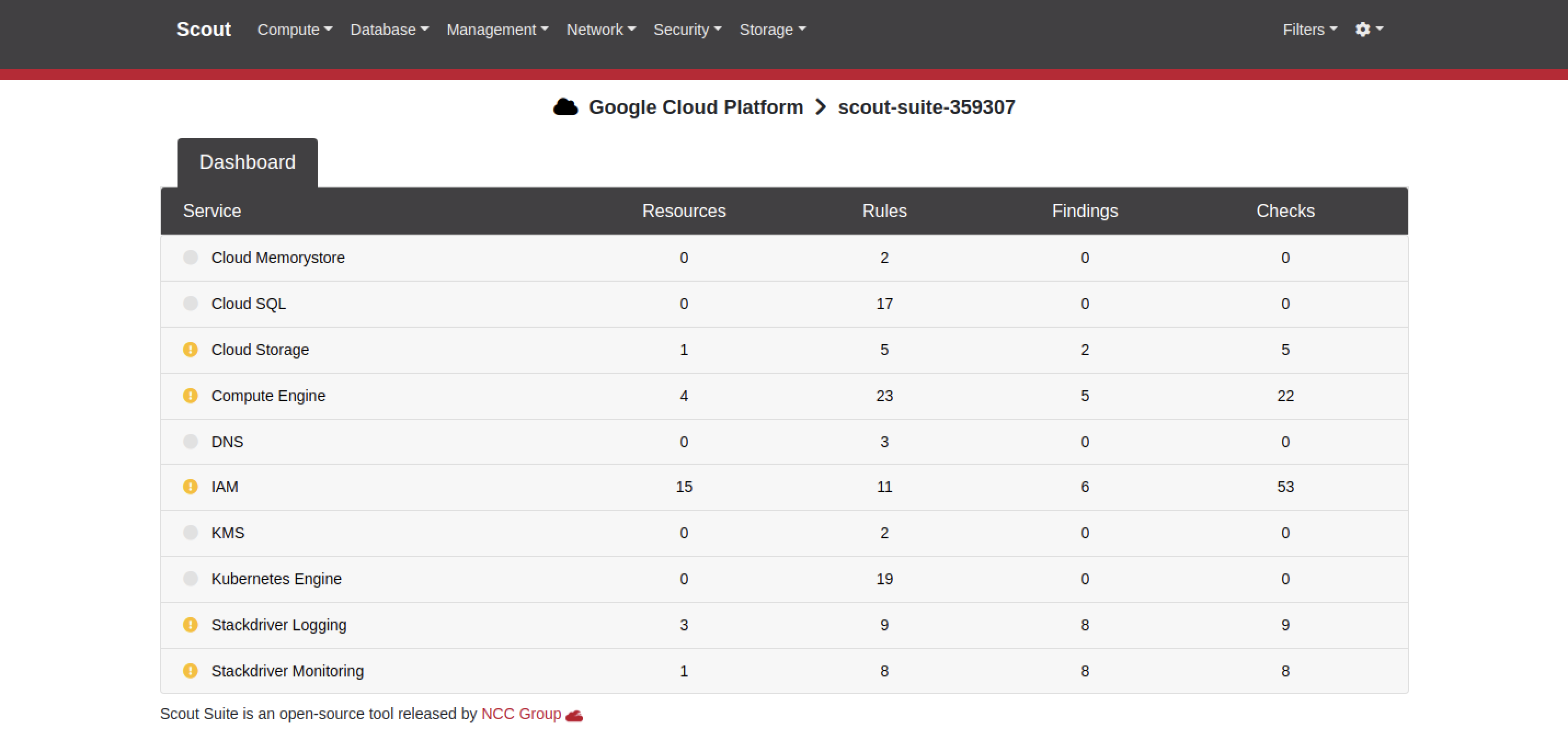
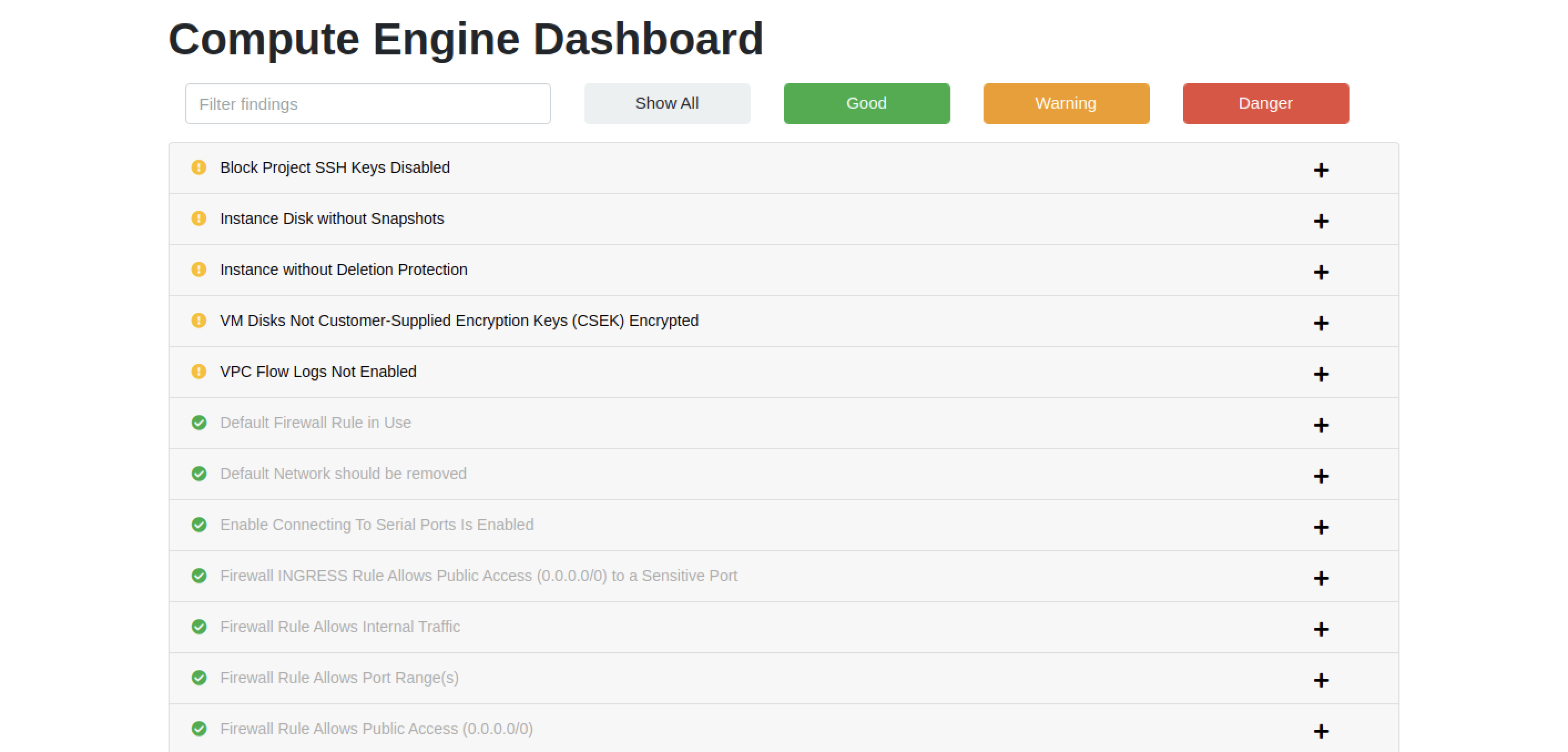
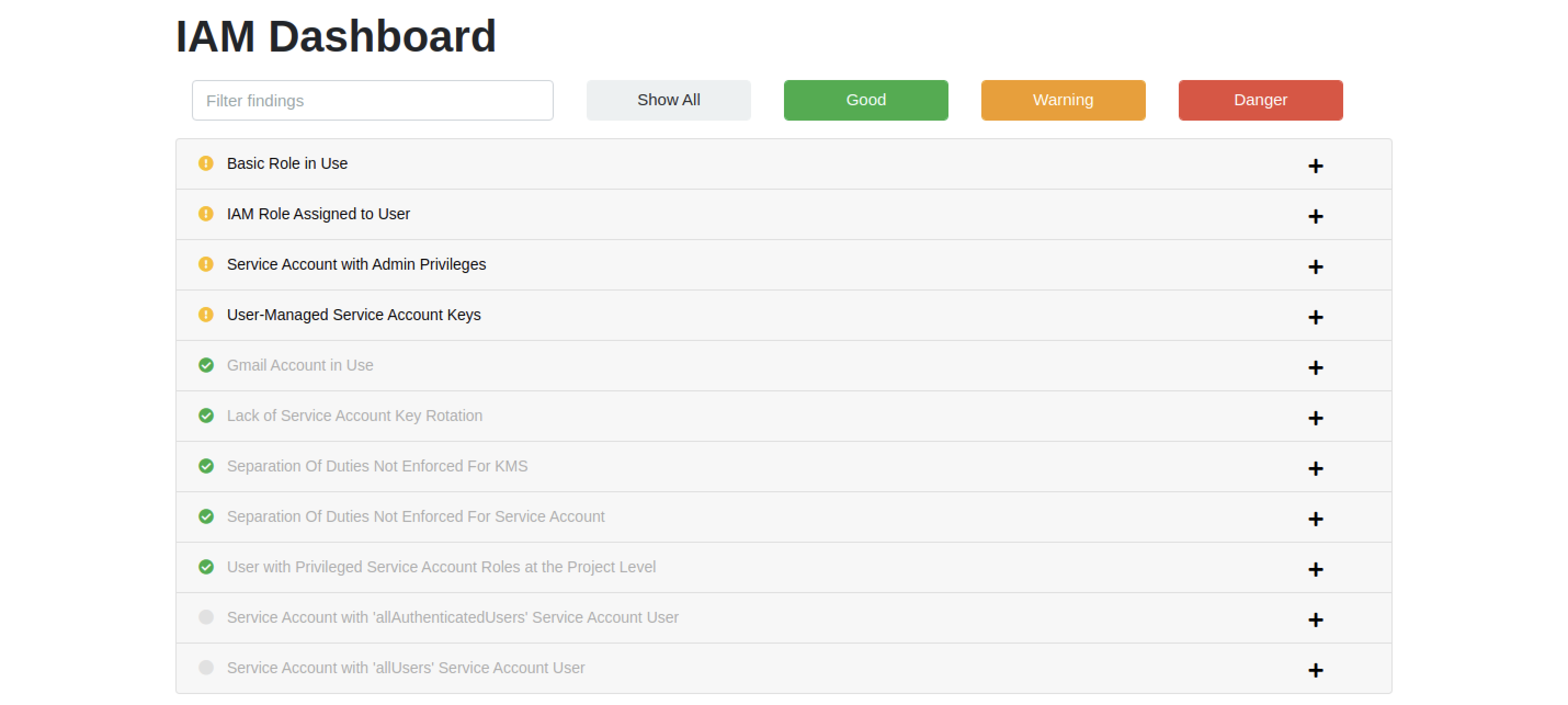
Here's a sample finding for Google Compute Engine - there is a clear description of the problem, along with remediation guidance and relevant references. You can click on the finding to get details on the resource(s) that violated this check.
Well, that's it. Scout Suite may not be a full-fledged replacement for commercial CSPM tools, but it is definitely a handy open-source tool to have in your arsenal.