What is FIDO2 WebAuthn?
A brief on FIDO2 WebAuthn, the latest authentication standard for web applications.
The security industry is quite good at conjuring acronyms that often leave you scratching your head. FIDO, OTP, 2FA, MFA, U2F, CTAP, TPM, USB, NFC, BLE - this is a veritable alphabet soup just for web authentication alone! In this post, I'll try to offer a mini-timeline of standards leading up to the latest in strong web authentication, errr WebAuthn.
What is FIDO U2F?
The FIDO (Fast IDentity Online) Alliance launched in 2013 to tackle the lack of interoperability among authentication devices and standards, with the stated goal of making life easy for users logging into web applications. You know, for us mortals who have to remember innumerable usernames and passwords. They started with the U2F protocol.
Universal 2nd Factor (U2F for short) is an open standard for augmenting two-factor authentication (2FA) using USB or NFC devices. It was initially developed by Google and Yubico, but is now hosted by the FIDO Alliance.
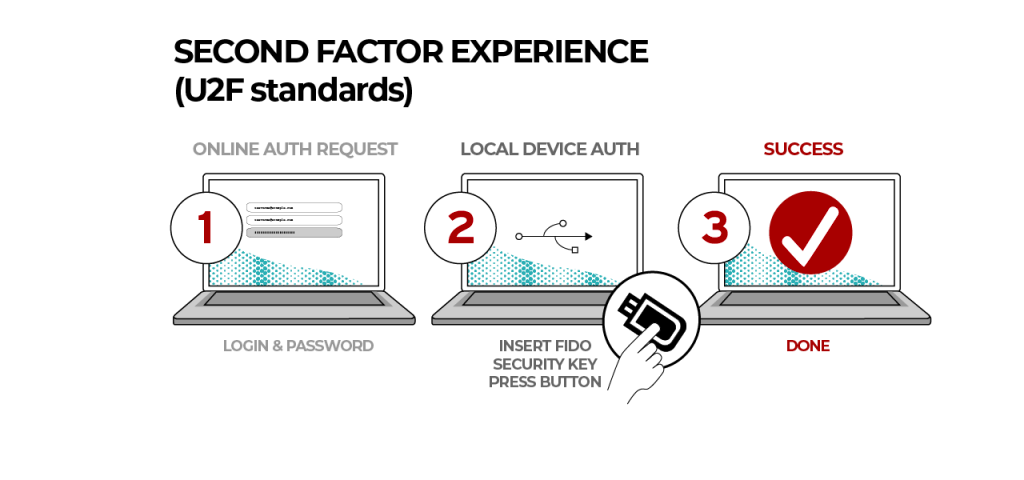
The USB devices establish communication with the computer using the HID protocol, which allows users to interact with client applications like web browsers by simply inserting the device into the computer. Each device has a unique secret key manufactured into it, and can respond to authentication challenges by applications using public-key cryptography. Popular devices include U2F security keys like Google Titan or Yubikey (supports FIDO2). Depending on your laptop/phone hardware, you may prefer a different Yubikey version - Yubikey 5 NFC for USB-A/NFC, Yubikey 5C NFC for USB-C/NFC or Yubikey 5Ci for dual USB-C/Lightning support.

How does FIDO Work?
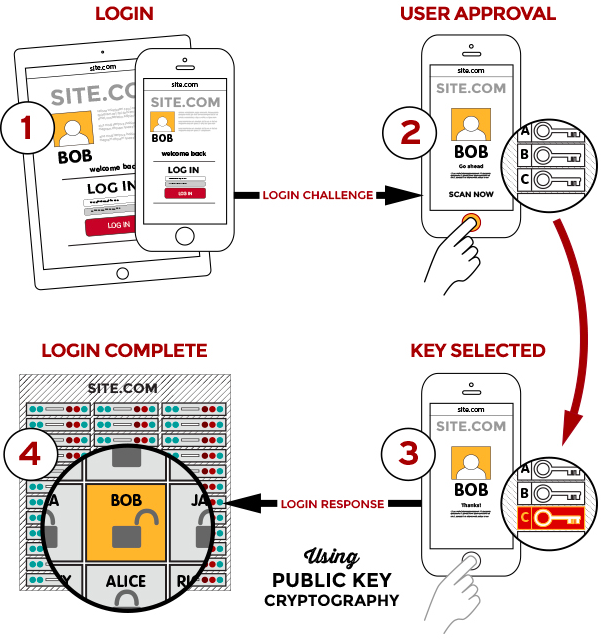
FIDO uses standard public-key cryptography techniques. During registration with a new service, the device creates a new public-private key pair. It stores the private key on the device itself, and registers the public key with the service. For each authentication request, the device unlocks the private key and signs a challenge after a user trigger like a finger swipe or a key press. Biometric information can also be used and is always stored locally, just like the private keys.
What is W3C WebAuthn?
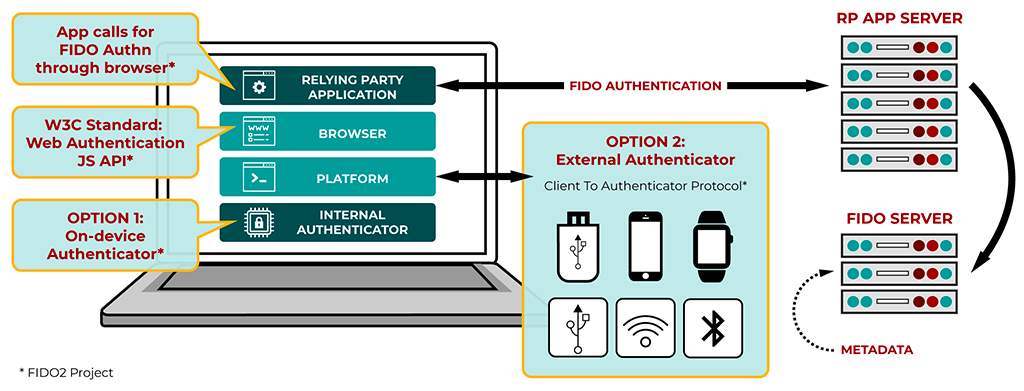
The U2F standard has undergone major revisions since launch, leading to the establishment of W3C WebAuthn and CTAP, which together form the basis of the FIDO2 standard and offer a complete replacement for U2F. A key difference between FIDO U2F and FIDO2 is that U2F was designed to be the second factor only, while FIDO2 devices can be used in single-factor mode too.
Web Authentication (WebAuthn for short) is a W3C standard for strongly authenticating users to web-based applications using public-key cryptography. Client to Authenticator Protocol (CTAP for short) allows devices like smartphones or hardware security keys to interoperate with client devices like laptops. In conjunction with CTAP, WebAuthn offers a replacement for U2F and is backward-compatible with U2F security keys.
FIDO2 strives to offer phishing-resistant web authentication, with support for passwordless, multi-factor options including PINs, biometrics, mobile and roaming hardware devices. FIDO2 devices are also resistant to malware attacks, as the private keys are stored on-device and are not accessible to the host computer.
Taking cue from companies like Google who have moved to mandatory FIDO2 security keys for all employees, I have started using Yubikeys with all supported websites. It's rather damning that most financial institutions (who claim bank-grade security) are still using SMS OTPs for authentication, and have shown no signs of supporting security keys. One can only hope that they implement WebAuthn soon, and not just pay lip service to end user security.