What is End-to-End Encryption (E2EE)?
A brief on end-to-end encryption, its pros and cons, and support from messaging platforms.
Encryption is a double-edged sword. On one hand, it is a foundational technology for protecting our privacy rights in an increasingly surveillance-heavy world. It helps to keep private information, well, private. On the other hand, it can also be misused for immoral, unethical and illegal purposes like child sexual abuse and human rights violations. In fact, this is the exact quandary that the European Union finds itself in today. Their well-intentioned bid to detect child sexual abuse material (CSAM) is leading to unintended privacy consequences for providers of end-to-end encrypted messaging platforms like WhatsApp.
Incredibly disappointing to see a proposed EU regulation on the internet fail to protect end-to-end encryption. https://t.co/1W1HixQUVJ
— Will Cathcart (@wcathcart) May 11, 2022
Source: Twitter
Encryption in transit is a term used to denote the encryption of communications between the sender and recipient using cryptographic protocols like TLS. For most services, separate encryption channels are set up between the sender and the service provider, and between the service provider and the recipient, with the service provider acting as a relay in between the sender and recipient. Now, this may be a desired outcome for providers of services like audio transcription, image classification, intelligent collaboration, content moderation etc, who need access to the unencrypted data to perform the services. However, this is not true end-to-end encryption and the service provider can, in theory, manipulate the traffic in transit without authorization too.
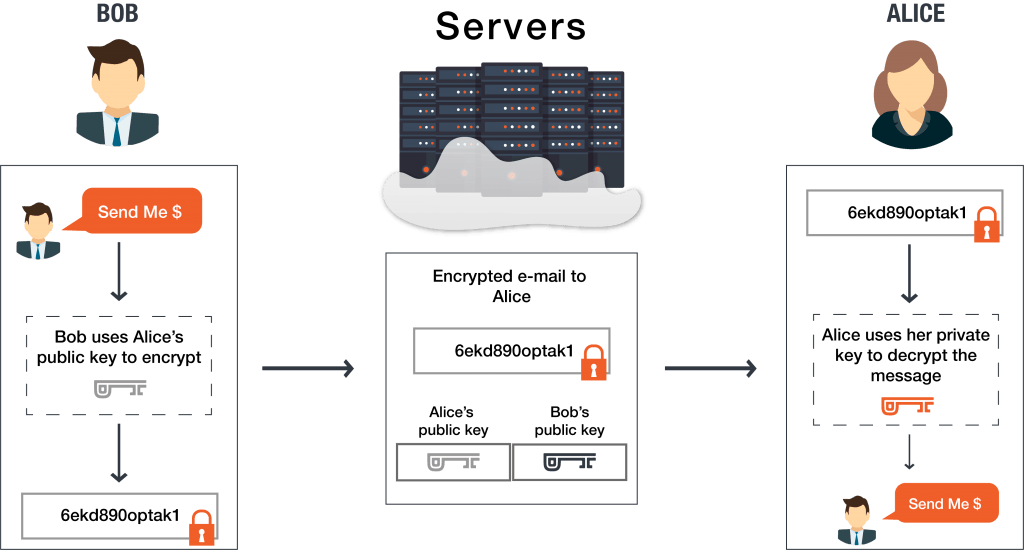
End-to-end encryption (E2EE) is a form of communication where the network traffic is fully encrypted in transit, even from the service provider, and can only be decrypted by the sender and recipient. It prevents communications from being intercepted or manipulated in transit using public key cryptography, and offers stronger guarantees on the confidentiality and integrity of the transmitted data.
As shown in the figure below, Bob uses Alice's public key to encrypt the message, and Alice uses her private key to decrypt the encrypted message (and vice versa). The service provider only stores the users' public keys to facilitate the communication, and does not have access to the users' private keys. Consequently though, the service provider may be unable to inspect and moderate the traffic for sensitive content or violations, and possibly run afoul of regulatory requirements.
Obviously, there are legitimate reasons for law enforcement and others to detect and stop the spread of harmful content too. This post will not attempt to review potential solutions or workarounds to resolve the inherent privacy quagmire. We will, however, look at some of the popular messaging platforms below and explore their support for E2EE communications.
While they did face some flak for enforcing phone number as a requirement for using the platform, Signal is still considered the best E2EE messaging client. In my opinion though, WhatsApp comes a close second. Despite the brouhaha around the updates to their terms of service and the inexplicably poor public communications, their choice of protocols used is still top notch and is explained in detail here.