Privileged Account Monitoring: 5 Hard Truths
A brief on the hard truths behind privileged access and its outsized role in modern breaches.
Security teams spend millions into taller walls and smarter gates, only to watch attackers slip through them with ease. Every new detection tool promises "more" - more visibility, more coverage, more alerts. But the attacker's playbook hasn't changed much: get in, find privileged credentials, move fast. Credential theft now accounts for 16% of initial access vectors in breach investigations, yet organizations keep chasing the next autonomous, AI-powered, quantum-resistant shiny tool instead of fixing the fundamentals.
The problem isn't lack of technology. It's that modern environments have become unwieldy. Hybrid cloud control planes, virtualised/containerised infrastructure, and distributed workloads have exploded with human and non-human identities. The result is complexity for defenders and opportunity for attackers - chaos as a ladder, in the classic sense. Littlefinger would be proud.

A recent Mandiant guide on privileged account monitoring lays out the scope of this problem and offers practical ways to tackle it. Drawing from that work, here are five uncomfortable but essential truths about securing your most valuable digital assets.
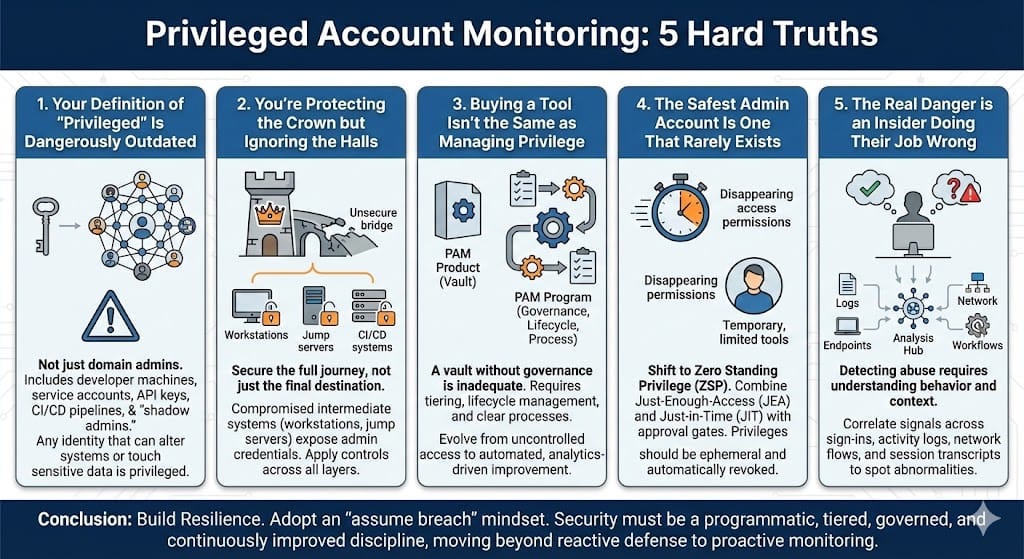
Your Definition of "Privileged" Is Dangerously Outdated
Most teams still think “privileged” means domain admins or global administrators. This narrow view leaves huge attack surfaces—developer machines, service accounts, API keys, CI/CD pipelines, business users with access to sensitive financial data, and "shadow admins" with indirect control—unguarded. A privileged identity is anything whose misuse causes real damage. If it can change systems, alter security policies, or touch sensitive data, it counts. Attackers know this. They often skip the obvious admin accounts entirely and go for these quieter targets because they're easier and just as useful.
You’re Protecting the Crown but Ignoring the Halls
Many security programs lock down admin accounts while leaving the paths to them wide open. Admins rely on workstations, jump servers, CI/CD systems, and other "intermediate systems". If any of these get compromised, the admin credentials come along on a Black Friday sale. A tiered model helps here: Tier 0 for identity systems, Tier 1 for critical business platforms, Tier 2 for standard user machines. The model is really about impact: secure the admin account all you want - if they are logging in from an unpatched Tier 2 laptop, game over. Securing privileged access means securing the full journey, not just the final destination, and applying controls across identities, endpoints, networks, and the application stack. No single weak link.
Buying a Tool Isn’t the Same as Managing Privilege
A Privileged Access Management (PAM) product is not a PAM program. Vaulting passwords without governance, tiering, lifecycle management, or clear processes leaves you only marginally better than the spreadsheets you replaced. You need to know who gets privilege, when, why, and for how long. Effective privilege management evolves through stages: uncontrolled access, ad-hoc fixes, consistent controls, and eventually automated, analytics-driven improvement. Mature programs don't just store credentials - they challenge whether those credentials should exist at all.
The Safest Admin Account Is One That Rarely Exists
Permanent admin rights create permanent exposure. The better model: give people access only when needed, only for as long as needed, and only the minimum permissions required. That's the core idea behind Zero Standing Privilege (ZSP) - combining Just-Enough-Access (JEA) to tighten scope, Just-in-Time (JIT) to limit duration, and approval gates to control issuance. Start at the endpoint with application control and endpoint management, which ensures only approved tools can run and elevate privileges. As PAM programs mature, privileges are delivered through time-bound role assignments or ephemeral credentials that are automatically revoked when the job is done.
The Real Danger is an Insider Doing Their Job Wrong
The hardest threat to detect isn’t an outsider breaking in—it’s a trusted user doing something unusual. Privileged abuse often looks like legitimate activity on the surface, which means the only way to spot it is by understanding behaviour and context. Effective monitoring correlates signals from sign-ins, conditional access, vault checkouts, endpoint activity, configuration logs, session transcripts, network flows, and workflow approvals to build context around who is doing what, when, and why. Without that correlation, abnormal activity goes unnoticed.
Conclusion: Build Resilience Before You Need It
Protecting your most powerful identities demands more than tools or outdated assumptions. It starts with an "assume breach" mindset and requires a broader definition of privilege, secure pathways end-to-end, a real governance program, a push toward zero standing privilege, and monitoring that understands human behaviour—not just system events. Security must be programmatic - tiered, governed, and continuously improved - rather than a one-time deployment. By layering controls and maintaining constant awareness, organizations shift from reactive defence to proactive resilience. The real question remains: do you truly know who holds the keys—and what they’re doing with them?