Lessons from CSRB's Review of the Microsoft Exchange Online Intrusion
A brief on the lessons learned from CSRB's review of the Microsoft Exchange Online intrusion.
Over the last decade and more, cloud service providers (CSPs) have become indispensable entities around the world, generating incredible efficiencies across industries, and enabling new products and services to be imagined and delivered quickly. Along the way, they have also become custodians of some of the most sensitive data in the world and, consequently, an attractive target for nation-state threat actors. It is probably fair to say that the CSPs have some of the best security controls across the board, but what happens when things go wrong? Well, Microsoft learned this the unfortunate way last year. In this post, I'll skim through the recent Cyber Safety Review Board (CSRB) report on a significant Microsoft intrusion from 2023, and pinpoint their key recommendations for organizations.
So, What Happened at Microsoft?
In 2023, Storm-0558, a hacking group associated with the People's Republic of China, compromised Microsoft's cloud environment, and used forged authentication tokens to access the email accounts of senior US government officials working on national security matters. During the course of this incident, Storm-0558 obtained a valid consumer Outlook Web Access signing key from 2016, and, in conjunction with another loophole in the system, was able to issue consumer key-signed tokens to gain access to Exchange Online enterprise email accounts. Needless to say, consumer and enterprise accounts should ideally be validated using different mechanisms, and this should not have been possible. Intriguingly, Microsoft has not yet determined how Storm-0558 obtained the signing key in the first place!
The report provides comprehensive details of the intrusion (you really should read it!), but here's a handy timeline for your reference:
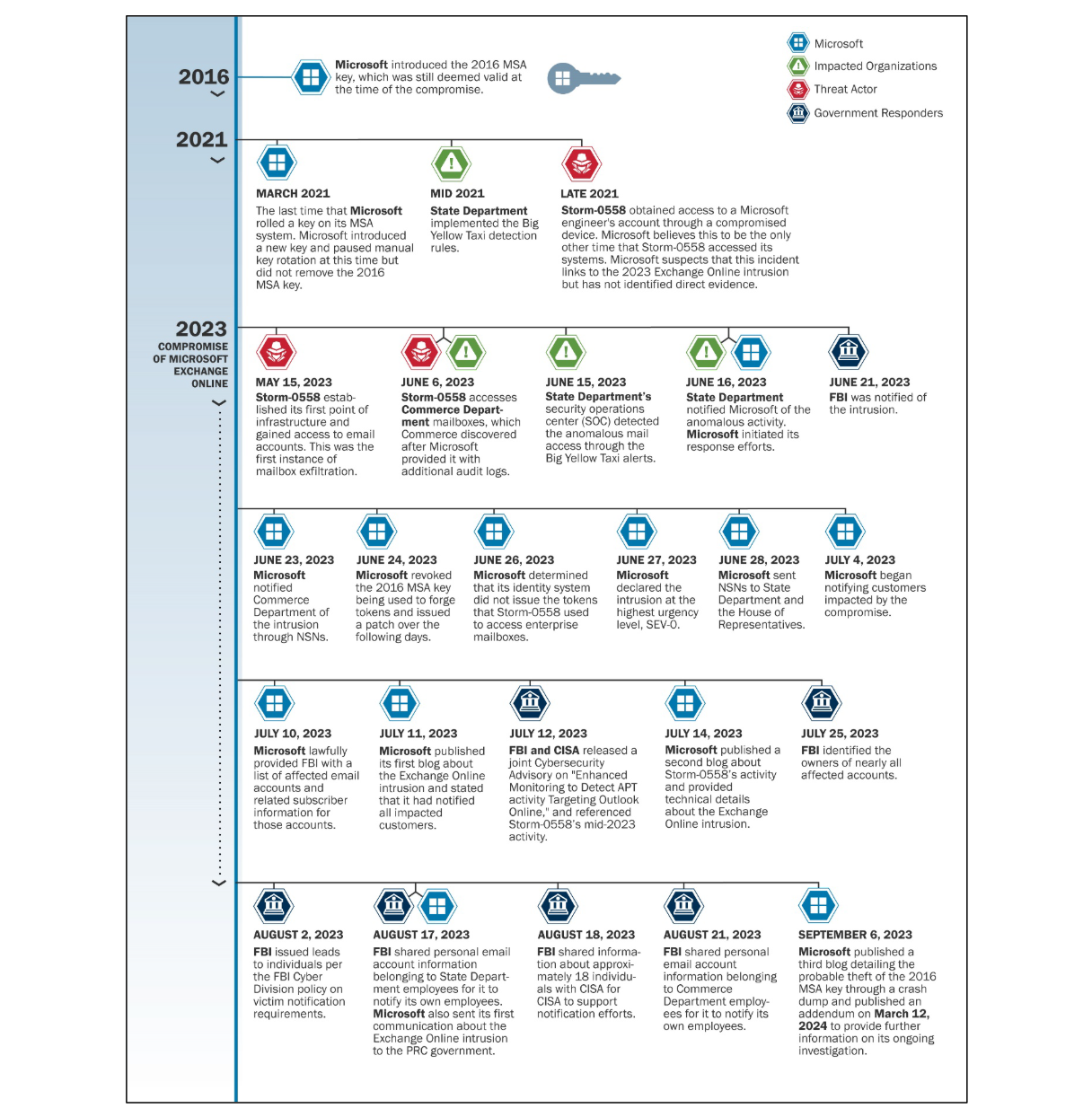
The CSRB was fully appreciative of Microsoft's cooperation during the investigation, but they found that the "intrusion was preventable and should never have occurred", and concluded that "Microsoft's security culture was inadequate and requires an overhaul". In particular, they highlighted:
- Failure to detect the compromise on its own
- Inadequate security practices compared to other CSPs
- Decision not to correct, in a timely manner, inaccurate public statements about the incident, including the root cause of the intrusion
- Operational and strategic decisions that "collectively point to a corporate culture that deprioritized security investments and rigorous risk management"
Lessons for Cloud Service Providers and Other Organizations
During the review, CSRB identified specific best practices that could materially improve the security of CSP digital identity systems, namely "automated regular key rotation; storage of keys in segmented and isolated key systems (e.g., hardware security modules [HSMs] or similar); use of stateful token validation; limiting scope of keys (e.g., to individual customers in some cases); use of proprietary data in token generation algorithms that could allow for detection of adversary-forged tokens that may not include such data; and the use of tokens bound to particular operations or sessions rather than broad bearer tokens."
CSRB also highlighted several broad recommendations for CSPs; frankly, most of these are excellent considerations for all organizations writ large:
- Make security a board-level priority; hold leaders accountable for defining and implementing security measures in a timely fashion.
- Create and uphold a strong security culture; include security by-design and by-default, not as an afterthought.
- De-prioritize feature development until security improvements are made commensurate with the assessed risks.
- Conduct rigorous threat modeling exercises commensurate with the criticality of the systems and data involved.
- Implement modern control mechanisms and baseline practices to reduce the risk of system-level compromise.
- Implement emerging digital identity standards to secure cloud services.
- Adopt minimum standard for default audit logging in cloud services; this should not be driven solely by business or financial reasons.
- Implement periodic compromise assessment and remediation procedures.
- Adopt transparent incident and vulnerability disclosure practices.
- Develop effective victim notification and support mechanisms.
- Promptly correct any factual inaccuracies in public or customer statements.